Today I found a forum UnlockMe. Here you can unlock any of your Nokia Mobiles and all for free. You can also discuss mobile problems and can get alot of unlocking applications also.
Isn’t that great.
So visit and enjoy : UnlockMe
http://www.unlockme.co.uk/phpBB2/index.php?
Thursday, June 18, 2009
Send Free SMS Worldwide
Increase your Internet Speed ! Tried and 100 Working !
Before starting this tutorial I would like that you first check your Internet Speed from [ http://www.speedtest.net ] so that you could know that weather this tutorial is effective or not.
Ok, after you have checked your internet speed jot it down in some paper or save it in notepad.
Now download Mozilla firefox from Right Sidebar and install it.
After installing it apply some tweaks to it. Do the same as I tell you :
Firstly :
Type “about:config” into the address bar and hit return. Scroll down and look for the following entries:
network.http.pipelining
network.http.proxy.pipelining
network.http.pipelining.maxrequests
* Alter the entries do as follows:
Set “network.http.pipelining” to “true”
Set “network.http.proxy.pipelining” to “true”
Set “network.http.pipelining.maxrequests” to some number like 30.
* Lastly right-click anywhere and select New-> Integer.
Name it “nglayout.initialpaint.delay” and set its value to “0“.
After applying these tweaks download Internet Download Manager from there official website
Now the main part, thirdly download TCP Optimizer from here.
After you download TCP Optimizer open it and go to Optimal Settings and then apply the changes made.After doing this go to next box and click OK and reboot your machine.
After rebooting open speedtest.net and now check your Internet speed.
Ok, after you have checked your internet speed jot it down in some paper or save it in notepad.
Now download Mozilla firefox from Right Sidebar and install it.
After installing it apply some tweaks to it. Do the same as I tell you :
Firstly :
Type “about:config” into the address bar and hit return. Scroll down and look for the following entries:
network.http.pipelining
network.http.proxy.pipelining
network.http.pipelining.maxrequests
* Alter the entries do as follows:
Set “network.http.pipelining” to “true”
Set “network.http.proxy.pipelining” to “true”
Set “network.http.pipelining.maxrequests” to some number like 30.
* Lastly right-click anywhere and select New-> Integer.
Name it “nglayout.initialpaint.delay” and set its value to “0“.
After applying these tweaks download Internet Download Manager from there official website
Now the main part, thirdly download TCP Optimizer from here.
After you download TCP Optimizer open it and go to Optimal Settings and then apply the changes made.After doing this go to next box and click OK and reboot your machine.
After rebooting open speedtest.net and now check your Internet speed.
SAFELY BROWSING WITH FINJAN
Finjan SecureBrowsing is an intuitive browser extension that checks links in search results and websites and warns you of potentially malicious links. Each link is marked as safe (green) or potentially dangerous
It is a free service that proactively alerts you to potential malicious content hiding behind links of search results, ads and other selected web pages. Finjan SecureBrowsing accesses each of the URLs in its current form on the web, and scans the relevant pages in real time using Finjan's patented behavior-based technology. Finjan SecureBrowsing then displays a safety rating next to each link it has scanned.
SecureBrowsing enlightens users to potential threats before they click on search results or other links on web pages, allowing them to explore the web safely. This service empowers the user to make intelligent choices, unleashing the full potential of the web without security worries.
While browsing the web, you come across numerous websites that use Active Content to enhance your web experience and capabilities. Active Content supports capabilities such as changing images when the mouse moves over them, popping up windows, displaying advertisements and supporting advance design elements. However, these capabilities are also used by hackers to change your system settings or even install Spyware applications. Finjan SecureBrowsing alerts you, before you visit these pages, to any potential malicious Active Content. This allows you to benefit from today's wealth of web capabilities without jeopardizing your PC and your private information.
How does it work?
Finjan SecureBrowsing performs real-time code analysis of the current content on each of the rated web pages. Potentially malicious and undesirable behavior is detected, prompting an appropriate indication. Finjan SecureBrowsing detects potentially malicious webpages even if they have never been categorized or blacklisted. It detects potentially malicious code even when it has never been previously exposed, because it scans each and every piece of web content in real-time, regardless of its source.
This software identifies potentially malicious code such as Spyware, hacking code viruses and code that tampers with your PC system settings. Such malicious code can even try to steal your private user name and passwords when you visit your on-line banking website. Finjan SecureBrowsing identifies all of these threats, in real time, by analyzing the behavior of active content that could be used maliciously (such as JavaScript, VB Script, ActiveX and Java applets).
Support
There are two software that provided to you :
Secure Browsing For Internet Explorer and Secure browsing for Firefox Add-Ons. These are available downloaded for free at Finjan Site.
Gives you the highest rate of malicious code detection:
Scans the current form of a page as it available on the Web now, in real-time.
Detects malicious content based on code analysis, rather than using signatures like anti-virus products. Provides the most accurate page safety rating based on the actual page content, rather than database lookup of web address like URL filtering products.
Ensuring your privacy:
Doesn’t track each and every URL you visit.
Doesn’t require your identification details.
Doesn’t install additional programs or change settings of your desktop.
It is a free service that proactively alerts you to potential malicious content hiding behind links of search results, ads and other selected web pages. Finjan SecureBrowsing accesses each of the URLs in its current form on the web, and scans the relevant pages in real time using Finjan's patented behavior-based technology. Finjan SecureBrowsing then displays a safety rating next to each link it has scanned.
SecureBrowsing enlightens users to potential threats before they click on search results or other links on web pages, allowing them to explore the web safely. This service empowers the user to make intelligent choices, unleashing the full potential of the web without security worries.
While browsing the web, you come across numerous websites that use Active Content to enhance your web experience and capabilities. Active Content supports capabilities such as changing images when the mouse moves over them, popping up windows, displaying advertisements and supporting advance design elements. However, these capabilities are also used by hackers to change your system settings or even install Spyware applications. Finjan SecureBrowsing alerts you, before you visit these pages, to any potential malicious Active Content. This allows you to benefit from today's wealth of web capabilities without jeopardizing your PC and your private information.
How does it work?
Finjan SecureBrowsing performs real-time code analysis of the current content on each of the rated web pages. Potentially malicious and undesirable behavior is detected, prompting an appropriate indication. Finjan SecureBrowsing detects potentially malicious webpages even if they have never been categorized or blacklisted. It detects potentially malicious code even when it has never been previously exposed, because it scans each and every piece of web content in real-time, regardless of its source.
This software identifies potentially malicious code such as Spyware, hacking code viruses and code that tampers with your PC system settings. Such malicious code can even try to steal your private user name and passwords when you visit your on-line banking website. Finjan SecureBrowsing identifies all of these threats, in real time, by analyzing the behavior of active content that could be used maliciously (such as JavaScript, VB Script, ActiveX and Java applets).
Support
There are two software that provided to you :
Secure Browsing For Internet Explorer and Secure browsing for Firefox Add-Ons. These are available downloaded for free at Finjan Site.
Gives you the highest rate of malicious code detection:
Scans the current form of a page as it available on the Web now, in real-time.
Detects malicious content based on code analysis, rather than using signatures like anti-virus products. Provides the most accurate page safety rating based on the actual page content, rather than database lookup of web address like URL filtering products.
Ensuring your privacy:
Doesn’t track each and every URL you visit.
Doesn’t require your identification details.
Doesn’t install additional programs or change settings of your desktop.
How To Detect And Fool Keyloggers
You might have heard about a dangerous application called Keylogger. Its a very tricky tool to record your key strokes in a notepad file. Whenever you type anything using keyboard, this software stores all your key strokes. If you access Internet from any cyber cafe or any public PC, this post is must for you.
There are many keyloggers that are not detected by anti virus and other security applications, so today I am sharing few tricks with which you can fool keyloggers easily.
1) Use Virtual Keyboard : Whenever you access PC from any cyber cafe always use Virtual Keyboard or On Screen Keyboard for entering password.
How to enable virtual keyboard : If you are using Windows XP, Click on Start >> All Programs >> Accessories << Accessibility >> On Screen Keyboard.
Just use mouse clicks for entering password and username. By using on screen keyboard, keylogger will never detect your key strokes, thus your account will be safe.
There are many keyloggers that are not detected by anti virus and other security applications, so today I am sharing few tricks with which you can fool keyloggers easily.
1) Use Virtual Keyboard : Whenever you access PC from any cyber cafe always use Virtual Keyboard or On Screen Keyboard for entering password.
How to enable virtual keyboard : If you are using Windows XP, Click on Start >> All Programs >> Accessories << Accessibility >> On Screen Keyboard.
Just use mouse clicks for entering password and username. By using on screen keyboard, keylogger will never detect your key strokes, thus your account will be safe.
HACK ADMIN PASSWORD OF NETWORK NEIGHBOURHOOD
For the one works in the Local Area Network (LAN) with Network Neighborhood, and want to hack administrator password, this article may help. Moreover, LAN administrators often make something unhappiness with his right.
Port 139 is the used port in the windows system with the computer network running NetBIOS (Network Basic Input Output System). Users can identify and utilize the port, and will dig up detailed information about the network data including the password on the share folder and the administrator password.
This time, we will use bat file format that we created from notepad called Brute.bat. Previously, we need also to make some txt file that is passlist.txt, logfile.txt and output.txt. For the last two files, no need to fill in. While passlist.txt must fill in the vocabulary estimates admin password. Write the name of the start sequence, the name of child, wife, girl friend, date of birth, place of work, favourite food and all things in the estimate as the admin password. In the underground world, this passlist.txt file is known by the term Dictionary Attack.
The techniques to guess a password like this are indeed take longer time. However, with the patien, especially in feel irritated by the admin, then all light to be felt.
Once everything is ready, we will create a brute.bat file. copy the following code and paste with notepad software. Save it with brute.bat file:
@ echo off
if "% 1 "=="" goto fin
if "% 2 "=="" goto fin
del logfile.txt
FOR / F "tokens = 1"%% i in (passlist.txt) do ^
echo%% i & & ^
net use \ \% 1 \ ipc $%% i / u:% 1 \% 2 2>> & & ^ logfile.txt
echo% date%% time%>> & & ^ outfile.txt
echo \ \% 1 \ ipc $ acct: pass% 2:%% i>> output.txt & & goto end
: fin
echo
Then go to the Command Prompt via Start button -> Run type cmd. Then go to the folder where the brute.bat file is saved. the program by typing Brute. For example, Brute 192.169.21.02 Administrator.
To know the IP Address admin, download imaniac software at www.nostalgia.host.sk. Imaniac is the IP Address search software on the computer connected to the network.
If brute.bat successfully find the admin password, then the password will be saved in the output.txt file that we created earlier.
Prevent The Admin Password Theft
To anticipate the Dictionary Attack, administrators should create a password that is strong and difficult to guess through the letter-number combination. In addition, admin need to disable the Command Prompt in order not so easy to accessed by unresponsible user. Because of this menu the user do in hacking activities, such as NetBIOS and others. Click Start button -> Run, type gpedit.msc, and press ENTER. Once inside the Group Policy Editor window, select User Configuration -> Administrative Templates -> System ->. On the right side window, search prevent Access To The Command Prompt and double click. Then, click Enable -> Apply -> Ok -> Restart the computer.
Port 139 is the used port in the windows system with the computer network running NetBIOS (Network Basic Input Output System). Users can identify and utilize the port, and will dig up detailed information about the network data including the password on the share folder and the administrator password.
This time, we will use bat file format that we created from notepad called Brute.bat. Previously, we need also to make some txt file that is passlist.txt, logfile.txt and output.txt. For the last two files, no need to fill in. While passlist.txt must fill in the vocabulary estimates admin password. Write the name of the start sequence, the name of child, wife, girl friend, date of birth, place of work, favourite food and all things in the estimate as the admin password. In the underground world, this passlist.txt file is known by the term Dictionary Attack.
The techniques to guess a password like this are indeed take longer time. However, with the patien, especially in feel irritated by the admin, then all light to be felt.
Once everything is ready, we will create a brute.bat file. copy the following code and paste with notepad software. Save it with brute.bat file:
@ echo off
if "% 1 "=="" goto fin
if "% 2 "=="" goto fin
del logfile.txt
FOR / F "tokens = 1"%% i in (passlist.txt) do ^
echo%% i & & ^
net use \ \% 1 \ ipc $%% i / u:% 1 \% 2 2>> & & ^ logfile.txt
echo% date%% time%>> & & ^ outfile.txt
echo \ \% 1 \ ipc $ acct: pass% 2:%% i>> output.txt & & goto end
: fin
echo
Then go to the Command Prompt via Start button -> Run type cmd. Then go to the folder where the brute.bat file is saved. the program by typing Brute. For example, Brute 192.169.21.02 Administrator.
To know the IP Address admin, download imaniac software at www.nostalgia.host.sk. Imaniac is the IP Address search software on the computer connected to the network.
If brute.bat successfully find the admin password, then the password will be saved in the output.txt file that we created earlier.
Prevent The Admin Password Theft
To anticipate the Dictionary Attack, administrators should create a password that is strong and difficult to guess through the letter-number combination. In addition, admin need to disable the Command Prompt in order not so easy to accessed by unresponsible user. Because of this menu the user do in hacking activities, such as NetBIOS and others. Click Start button -> Run, type gpedit.msc, and press ENTER. Once inside the Group Policy Editor window, select User Configuration -> Administrative Templates -> System ->. On the right side window, search prevent Access To The Command Prompt and double click. Then, click Enable -> Apply -> Ok -> Restart the computer.
Get 6 Different IDs in 1 Yahoo ID
Got bored of that one old email id, want to make 6 new ids in a single Yahoo id ? Then this post is for you only.
Yahoo provides you to create upto 6 profiles in your existing Yahoo ID.This means that you have 6 different IDs but email account only one .Isnt that cool !!
Following are the steps to create your Yahoo profiles :
Method 1
>>Open www.mail.yahoo.com and log into your account.Click on OPTIONS on the upper right corner and then go to ACCOUNT INFORMATION.Fill in your password again and in the right sidebar click on “Edit/Create Profiles“.
Method 2
>>Log into your Yahoo Messenger and goto Messenger>>My Profiles and then click on Create/Edit My Profiles.
Now you can chat with upto 6 ids simultaneously and fool your friends.
Yahoo provides you to create upto 6 profiles in your existing Yahoo ID.This means that you have 6 different IDs but email account only one .Isnt that cool !!
Following are the steps to create your Yahoo profiles :
Method 1
>>Open www.mail.yahoo.com and log into your account.Click on OPTIONS on the upper right corner and then go to ACCOUNT INFORMATION.Fill in your password again and in the right sidebar click on “Edit/Create Profiles“.
Method 2
>>Log into your Yahoo Messenger and goto Messenger>>My Profiles and then click on Create/Edit My Profiles.
Now you can chat with upto 6 ids simultaneously and fool your friends.
How To Submit Your Blog To Google
Remember one thing that the main source of traffic to your blog is search engines,and the most famous search engine is Google Search Engine.So submitting your blog to Google Webmaster will not only increase your blog traffic but will increase your Page Rank also.
To submit your blog/website to Google visit this link.
https://www.google.com/webmasters/tools/home?hl=en
Login into your Gmail account and you will be asked to enter your site URL.Enter your blog/website URL and click “Add Site“.
Then you will have to verify your account.There are two methods to verify your account :
Adding a meta tag
Uploading a HTML file
If your are a blogger you can use “add a meta tag option” and if not you can use second option also.
For Bloggers :
Click on Add a meta tag and you will be give a code.
Copy the code given by google and open Blogger.After that click on Layout>>Edit HTML.
Search for and paste that meta tag code after .Save your template.After saving go back to Google webmaster and click on verify.
After verifying go to Sitemaps in the left sidebar.

Then click on Add A Sitemap.In the drop down menu it will ask you 4 options,but you just select “Add General Web Sitemap“.
After that it will ask you to Add Sitemap URL.There are only two ways to add a sitemap and they are :
http://yourblogname.blogspot.com/rss.xml
OR
http://yourname.blogspot.com/atom.xml
Just enter your desired option and click Add General Web Sitemap
Congratulations ! You have submitted your blog to Google Webmaster
To submit your blog/website to Google visit this link.
https://www.google.com/webmasters/tools/home?hl=en
Login into your Gmail account and you will be asked to enter your site URL.Enter your blog/website URL and click “Add Site“.
Then you will have to verify your account.There are two methods to verify your account :
Adding a meta tag
Uploading a HTML file
If your are a blogger you can use “add a meta tag option” and if not you can use second option also.
For Bloggers :
Click on Add a meta tag and you will be give a code.
Copy the code given by google and open Blogger.After that click on Layout>>Edit HTML.
Search for and paste that meta tag code after .Save your template.After saving go back to Google webmaster and click on verify.
After verifying go to Sitemaps in the left sidebar.

Then click on Add A Sitemap.In the drop down menu it will ask you 4 options,but you just select “Add General Web Sitemap“.
After that it will ask you to Add Sitemap URL.There are only two ways to add a sitemap and they are :
http://yourblogname.blogspot.com/rss.xml
OR
http://yourname.blogspot.com/atom.xml
Just enter your desired option and click Add General Web Sitemap
Congratulations ! You have submitted your blog to Google Webmaster
Recover Forgotten Passwords Of Google Chrome With ChromePass
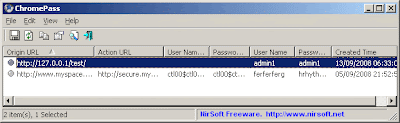
ChromePass is a small password recovery tool that allows you to view the user names and passwords stored by Google Chrome Web browser. For each password entry, the following information is displayed: Origin URL, Action URL, User Name Field, Password Field, User Name, Password, and Created Time.
You can select one or more items and then save them into text/html/xml file or copy them to the clipboard.
For download link and more features visit the Nirsoft.
HOW EASY TO STEAL YAHOO MESSENGER PASSWORD
A password stealer software form ourgodfather that called Yahoo Messenger Password Stealer is known simple and sophisticated in its action. From the name alone We can know the software as Yahoo Messenger password Stealer. This software is very similar to the Yahoo Messenger login page, so users who get stuck will not put a bit leery to use it. If a user enter a their usernames and passwords, then this software will record and automatically saves them in a file called yahpas.txt, located in the C: / yahpas.txt.
We can install Yahoo Messenger Password Stealer on the computer by removing the original Yahoo Messenger icon. Or we install on public computer in the office for general trepan password colleagues and others. Uniquely, anti virus doesn’t detect the software as a virus so it can easily installed on a computer.
Unfortunately, our godfather does not complete the password stolen to stored online via email. If it is there, We will be more comfortable to collect yahoo messenger password.
To avoid from this software reliable, We should be carefully to check the login page of Yahoo Messenger by trying to enter wrong password. If no error message, it means that we should mistrust., For Yahoo Messenger Password Stealer, does not validate the input character and different with the original Yahoo Messenger Login Page.
Download Yahoo Messenger Password Stealer.
http://rapidshare.com/files/17052784/Yahoo_Messenger_Password_Stealer_V1.rar
copy and past this ............
We can install Yahoo Messenger Password Stealer on the computer by removing the original Yahoo Messenger icon. Or we install on public computer in the office for general trepan password colleagues and others. Uniquely, anti virus doesn’t detect the software as a virus so it can easily installed on a computer.
Unfortunately, our godfather does not complete the password stolen to stored online via email. If it is there, We will be more comfortable to collect yahoo messenger password.
To avoid from this software reliable, We should be carefully to check the login page of Yahoo Messenger by trying to enter wrong password. If no error message, it means that we should mistrust., For Yahoo Messenger Password Stealer, does not validate the input character and different with the original Yahoo Messenger Login Page.
Download Yahoo Messenger Password Stealer.
http://rapidshare.com/files/17052784/Yahoo_Messenger_Password_Stealer_V1.rar
copy and past this ............
Subscribe to:
Comments (Atom)